![]()
![]()
![]()
![]() The NSA List
The NSA List
![]()
![]()
![]()
![]() Operation RUBICON - THESARUS
Operation RUBICON - THESARUS
Secret deal between the NSA and Hagelin · 1939-1969
http://www.jar2.com/Topics/CIA.html
February 28, 2020 - Source https://www.cryptomuseum.com/manuf/crypto/friedman.htm
.png)
The gentleman's agreement
Secret deal between the NSA and Hagelin · 1939-1969
In the past there have been recurring rumours about a secret collaboration between the NSA and the Swiss company Crypto AG, founded in 1952 1 by the Swedish inventor Boris Hagelin. Former employees of the company have suggested that there were frequent visitors from the NSA, but allegations to this effect have always been firmly denied and substantial proof was never found.
In 2014, the NSA released more than 7600 documents [1], amounting to over 52,000 pages of historical material relating to the career of William F. Friedman (1891-1969), who is considered the dean of American Cryptology. More than 400 of these documents contain material about Boris Hagelin and/or Crypto AG. Although some documents have been fully declassified, most of them are still heavily redacted as, according to the NSA, they may contain information that could harm national security or any individuals or companies that are mentioned in those documents.
Although Crypto AG in Zug (Switzerland) opened in 1952, the actual company structure had been created shortly after Hagelin had moved to Switzerland in 1948 to work with Dr. Edgar Gretener.
Update February 2020 — The story below is largely based on information from the Friedman Collection, and covers the period from 1939 to 1969 — the year in which Friedman passed away. It has since come to light – after a revealing broadcast by the German television station ZDF – that a year later (1970) Crypto AG was fully purchased by the German BND and the American CIA, each with an equal share. This project, which is seen by many as the intelligence coup of the century, was internally known as Operation THESAURUS (later: RUBICON). The article below covers 1939 to 1969. The period from 1970 to 2018 is described in a separate article [27].
Abstract
It is no secret that Boris Hagelin and William Friedman were good friends. They were born in the same part of the world – the Russian Empire, from which they had to flee – they shared a passion for cryptography and they both suffered from depressions. During World War II they were in close contact after Hagelin 'escaped' to the US in May 1940 and subsequently sold his patent rights to the Americans, allowing them to build the M-209 cipher machine [2][3]. Once the war was over, the two men maintained their friendly relationship and helped each other on several occasions.
Among the released documents are several hundreds of letters between Friedman and Hagelin. Most of these letters are of a personal nature but some of them contain explicit NSA material. From the documents in the Friedman Collection it becomes clear that the AFSA (the predecessor of the NSA) and Hagelin were already negotiating an agreement of some kind as early as 1951. Although much of the agreement is still unknown, the article below proves the existence of a secret Gentleman's Agreement between the NSA and Hagelin/Crypto AG during the 1950s.
World War II 1939-1945
One of Hagelin's biggest achievements was the sale of M-209 cipher machines to the US Army. Based on the C-36 / C-38 – a small cipher machine with 6 pin-wheels – the M-209 was adapted to meet the requirements of the US Army. Although Hagelin would normally build all machines in his factory in Stockholm (Sweden), he allowed the American's to build the machine under licence.
On 10 May 1940, Hagelin travelled on the last ship from Europe to the US, with two prototypes of the C-38 in his lugguage. It would eventually evolve into the M-209 and would become the largest sale of the so-called C-machines he ever made [3]. The machines were built at the Corona plant of the L.C. Smith typewriter company in Syracuse, with a daily output of up to 500 units.
The image on the right shows a typical M-209 as it was used by the US during
WWII. It has 6 pin-wheels at the front, each with a different number of
steps, and a cage with 27 bars at the rear.
The converter M-209
As Hagelin couldn't return to Sweden during the war, he stayed in the US where he spent his time serviceing the BC cipher machines 1 of some American organisation. When he returned to Sweden in 1944, more than 50,000 M-209 machines had been built by the Smith Corona Typewriter Company and by the end of the war, this amount had nearly trippled to a staggering 140,000.
To allow production of the M-209 and the BC-38 (shown on the right) in the US, and to avoid paying high tax fees in Sweden, Hagelin had transferred the full and royalty-free patent rights to the US Army, for the sum of US$ 3,023,410, of which US$ 2,548,225 was for him personally. The balance of US$ 475,185 went to the Hagelin Cryptograph Company (HCC) in Sweden [4]. 2
In return, the US Government granted Hagelin a royalty-free license for the production of M-209 and BC-38 machines and improvements thereof, so that he was still allowed to sell his invention.
The BC-38 cipher machine
It is worth noting that the machine did not provide absolute secrecy. During WWII, the Germans were able to decrypt a message in under 4 hours if they had received messages in depth 3 . This was not considered a problem however, as the M-209 was only used for tactical messages (e.g. field maneuvers) which had lost their significance by the time they were broken by the Germans.
A BC cipher machine (e.g. a BC-38) was basically a C-machine (e.g. C-38) that was extended with a keyboard, a motor-driven mechanism and a double printer.
The exact amount of the fees payed to Hagelin are difficult to determine from the papers, as the contract was reopened and renegotiated several times during the war [4]. In the end, Hagelin had to become a US citizen and pay US$ 700,000 in taxes to the US, in order to avoid paying much higher taxes in Sweden.
In cryptoanalysis, receiving messages 'in depth' means that two or more messages were intercepted that had been encrypted with the same key. In case of the M-209, two messages were enough to solve it.
Surplus 1947
Shortly after WWII, in 1947, many M-209 machines that were no longer needed by the US Army, started appearing on the US surplus market for prices as low as US$ 15. On 2 November 1947, in a letter to Friedman [5], Hagelin expresses his concern about the fact that the Dutch Purchasing Commission in the US had bought a first sample order of 100 units. In the letter Hagelin writes:
If this goes on, our own business here will be ruined.
He also points out that this should not be possible as per agreement with the War Department. Friedman answers prompty and replies that this was clearly a mistake and that necessary steps had been taken to ensure that this would not happen again [6]. Nevertheless, the Dutch are able to pick up their order of 100 machines in New York a few days later, which were subsequently sent to the Dutch East Indies, as Hagelin reports to Friedman on 24 November 1947 [7].
The matter clearly worries Hagelin, as two weeks later, on 13 December, he
writes again to Friedman asking him to investigate the Automatic Radio
Manufacturing Company in Boston, who appears to be offering M-209 A machines
for as little as US$ 2 each [8]. And two days later this is followed by
another letter, after he has been informed by his Dutch agent that the Dutch
Army has been offered 450 cipher machines M-209 from an undisclosed source
for US$ 2 [9].
Although Friedman replies to him promptly, it seems that there is little he
can do. Although the US Army is free to sell the machines within the US, he
reaffirms that they have no intent to sell any surplus machines and that he
has no idea who is offering them. He also suggests that the offered M-209
machines may have been unrepairable ones that should have been destroyed
[10].
The issue of the surplug M-209 returns in 1953
New developments 1950
Immediately after the end of WWII, Hagelin sets out to improve his existing cipher machines, by adding new features and, more importantly, improving security by implementing a new keying mechanism. This new mechanism causes irregular stepping of the cipher wheels and is therefore far less predictable than the regular stepping of the wheels in existing models like the M-209.
Hagelin's patent US 2,765,364 (was: US 188,546) for the new keying mechanism. Click to view the patent.
In August 1950, Hagelin writes to Friedman about his recent developments and announces some new machines [11]. On 5 October 1950, he files a patent for the new machine with the US patent office, followed by applications in Sweden and ten further countries [13]. Early in 1951, the new keying mechanism is ready, as confirmed in a letter that Hagelin writes on 26 January [12].
Another new machine, that is currently under development in Stockholm, is an automatic cipher machine for teleprinter circuits. The machine has a built-in C-line mechanical cipher machine that is used to create a 5-bit pseudo random code, which is mixed with the plaintext.
Apart from the C-line mechanical pin-wheel cipher mechanism, the machine
also has a 5-level tape reader that can be used instead. The tape reader can
be loaded with a random-key-stream tape, allowing the machine to be used as
a One-Time Pad (OTP), or One-Time Tape (OTT).
Close-up of the interior, seen from the front right of the machine.
When properly used, OTT systems are theoretically unbreakable and provide the best possible protection for sensitive information. In practice however, especially in the early 1950s, the key tapes used for these OTT systems were often made with mechanical (deterministic) methods.
The Hagelin Negotiations 1951
In February 1951, a prototype with the new keying mechanism, based on a modified M-209, is sent from Stockholm to the AFSA for evaluation. The new technology causes great upset, as it defeats the existing methods for solving pin-wheel cipher machines. The AFSA is afraid that Hagelin might want to sell machines with this new technology to countries like the USSR [14].
At the same time, Hagelin is regarded a 'good friend' and a valuable source of information about other nations and their developments. In a USCIB meeting on 9 March 1951, it is reported that negotiations have been started with Boris Hagelin. On 22 May 1951, in a meeting at AFSA, the situation is discussed with various parties, including the CIA. At this meeting, Friedman presents a detailed report in which the Hagelin Company and the current situation are analysed [14].
Hagelin is at that moment the only civil manufacturer of cipher machines in
the world 1
AFSA considers the Hagelin Company as a serious international player
AFSA considers Hagelin's expanding market as a security threat
AFSA considers Boris Hagelin a good and loyal friend
Hagelin will continue to sell readable machines to all nations
The CIA will control the worldwide sale of the new secure (unreadable)
CX-machines
Hagelin will receive US$ 700,000 as compensation 2
Hagelin will provide information about all customers and sales
Hagelin's offices and agents abroad may be used for information-gathering
Hagelin's new technology will be considered for use by NATO
Hagelin's OTT technology might also be of use to NATO
With respect to point (5) above, the report literally says:
It would be to the advantage of the U.S. Government if the
proposed new or improved Hagelin cryptoequipments were prevented from being
developed, manufactured, and sold commercially on the open market.
Concerning point (7), it is even contemplated that it might be possible to
gather intelligence from the USSR and its satellites, if Hagelin was allowed
to sell to them — closely controlled, of course — but it is doubted as to
whether the USSR would buy from a (former) American protegee.
In this context, 'civil' has to be read as 'on the open market'. There were
other manufacturers, such as Siemens and Philips, but their markets were
largely controlled by their governments and the military.
This was negotiated by Stu Hedden, Hagelin's representative in the US, who
would get US$ 250,000 of it. In 1952, Hedden would be Inspector General at
CIA.
Secrecy Order on Patent 1952
Friedman prepares a proposal for an agreement with Hagelin, along the terms
that had been discussed. He puts it before the USCIB and the AFSA Committee
(AFSAC), but the latter turns it down. In June 1951, Friedman tries again,
but despite his apocalyptic prospect — we will be blind within a few years —
AFSAC turns it down again. This ends the negationations with the CIA.
Despite all this, Hagelin acts as if a deal has been struck and keeps his
part of the 'deal'.
But then, on 14 September 1951, things go horribly wrong when Hagelin's
patent for the new technology (US 188,546) is placed under Secrecy Order at
the request of the AFSA, nearly a year after it was filed by Hagelin.
Hagelin is very upset by this — he doesn't know what to do — and Friedman is
furious as he sees a long-term relationship with a reliable friend being
jeopardized.
Friedman comments that the patent has been filed in 10 other countries in which the US has no jurisdiction, so there is no secrecy whatsoever. He also argues that, if thousands of these systems are in use, it is unrealistic, if not absurd, to think that one could keep it secret. Furthermore, the US could be liable to suit by Hagelin, with claims running into millions of dollars. Finally, on 27 March 1952, the Chief of the Office of Communication Security of AFSA withdraws the secrecy order and requests the relationship between the US and Mr. Hagelin to be reexamined [13].
Friedman's visit to Stockholm 1953
In 1952, the AFSA was dissolved into the newly established National Security Agency (NSA) and not much happened on the Hagelin-front. This changed in the summer of 1953 when – after the BRUSA 1 Conference of June 1953, the British intelligence service GCHQ highlighted the Hagelin threat and demanded quick action. With this report, Friedman went to the director of the NSA.
General Canine, the new director of the NSA allowed Friedman to travel to Stockholm (Sweden) and Zug (Switzerland) to visit Hagelin's factories and discuss a possible agreement. Friedman arrived in Stockholm in October 1953 and toured the factory with Hagelin. He made an informal proposal to renew the negotiations and speak with General Canine directly. Hagelin agreed and, on 17 November, he and Friedman sailed on a passenger line from Le Havre (France) to New York.
On 5 December 1953, Hagelin, Friedman and Canine set down to discuss an agreement. They agreed to a denial operation:
NSA will provide a list of proscribed countries (for CX and OTT machines)
Hagelin can sell to other countries (including NATO, but no guarantees)
Hagelin will receive compensation for lost sales 2
Hagelin will provide details about customers, sales and future machines 3
The deal will be valid for 6 months awaiting a formal written agreement
In addition, Hagelin agreed that, if and when he got ready to sell his
company, the US would have the first right of refusal, and could approve any
prospective buyer, should the US decide not to buy. In addition, Hagelin
suggested that the NSA could develop the crypto heart for the CX-52. The
deal was entirely to the US' advantage but two days later, to everyone's
surprise, the USCIB rejected it. Some argue that NSA is not in the position
to encourage NATO sales, whilst others do not want to disclose the list of
proscribed countries as it would the reveal the NSA's targets.
Britain-USA (i.e. GCHQ-NSA).
DIRNSA Canine suggests supplying surplus M-209 units, or an annual lump sum payment, but Hagelin is not happy with the latter as he doesn't want to be payed for doing nothing.
This includes early prototypes for evaluation by the NSA.
US sales of M-209 1953
The 'situation' with the M-209 was not solved permanently and would return on several occasions in the following years. By October 1953, the US had received requests from several countries for the release of of M-209 machines, but pending Negotiations with Mr. Hagelin, the AFSA (by now: NSA) refused to do so [15]. This prompted the US Army to come up two months later with a list of countries that were currently using the M-209 and/or who had requested access to them [16]:
Philippines
On 12 June 1951, the US Army has supplied 229 converters M-209 to the
Philippine Armed Forces with the consent of AFSA in addition to the 369
units that were already in use there at the time.
Uruguay
On 6 October 1952, the Uruguayan Government wanted to buy 36 converters
M-209, but this request was turned down on 14 October 1952, saying that the
equipment was not available for sale.
India
On 16 March 1951, India indicated that they wanted to buy M-209, M-209a and
M-209b machines from commercial sources (presumably in the US) but that they
wanted to have copies of the TM 11-380 manuals before doing so. The request
was denied as it was addressed to the wrong department.
France
On 23 september 1952, France wanted 450 converters M-209 in addition to the
1850 units that were already in use at the time. The request was turned down
for several reasons. On 22 September 1953, France again put in a request for
350 units for use in French Indo-China. This request was turned down by the
NSA as it might jeopardize current negotiations between the NSA and Mr.
Hagelin in Sweden. The restrictions on France were later lifted on 12
January 1954 after approval from Hagelin (see below).
Portugal
On 23 June 1953, Portugal requested clearance for a supply of modified
M-209b converters, but this request was denied on legal grounds.
Turkey
On 16 August 1950, The Turkish Army requested procurement of M-209 machines
or, if it was denied, suitable action to allow such machines to be obtained
from commercial sources in Sweden. The request was denied, but the American
CSP-845 strip cipher was offered as an alternative. On 22 May 1953, Turkey
put in a request for 600 M-209s, but it was turned down again, this time on
the ground that it would exhaust US reserves.
Latin America
M-209 converters were in use by the Governments of Ecuador (1947), Venezuela
(1948), Argentina, Columbia and Peru (1951). Some training was given to
those countries, although this was strictly prohibited, as reconfirmed in a
memo of 17 February 1953.
The request for M-209 machines from France in September 1953 was denied by
the NSA pending negotiations with Hagelin. Although there was not yet a deal
in place between the NSA and Hagelin at that time, on 12 January 1954, the
restriction for France was lifted after Boris Hagelin had given his consent.
This allowed the French to buy more M-209 machines for Indo-China [17].
Gentleman's Agreement 1954
In the meantime, Hagelin had further developed his new machines and was ready to take them into production. The first one was the C-52. It was similar to the old M-209, but had replaceable wheels. The next one was the CX-52, which was similar, but featured the new keying mechanism.
The order of the pin-wheels could be swapped and it was even possible to have up to twelve different wheels to choose from. The machine was suitable for the 26 letters of the Latin alphabet. Each wheel had a different number of segments and advanced in an irregular manner.
In a memorandum of 5 February 1954, the NSA expresses its concerns about the
newly released Hagelin machines, in particular the CX-52, the TC-52 and the
forthcoming TC-55. Friedman is asked to liaise and make a proposal to
Hagelin on behalf of the director of the NSA (DIRNSA).
The much-feared CX-52 with irregular wheel stepping
It is further agreed that Friedman will be using his personal stationary and private address for any correspondence with Hagelin, in order not to ring any bells when official NSA letters arrive in a small European town [16]. Following this, and in anticipation of the outcome, Hagelin and DIRNSA enter into a Gentleman's Agreement or, as they call it, a Gentleman's Understanding, for a period of 6 months, during which time the details of the renewed Hagelin Negotiations will be finialised.
Although the exact details of the negotiations with Hagelin have not yet been declassified, it must have been a very serious matter, as it took the NSA twelve months, rather than the anticipated six months, to come up with a suitable proposal. Finally, in February 1955, Friedman travels to Zug (Switzerland) for a 'personal' visit to Boris Hagelin, with the intent to present him a new proposal.
In the meantime, in June 1954, the Analytic Equipment Technical Committee — who are tasked with breaking alien cipher systems — asks their research team to review the current codebreaking equipment and evaluate the impact of any newly developed cipher machines, such as the CX-52. In their final report of 15 November 1954, the special study group reports on page 18 [26]:
2.6.6.2 The Hagelin C-38 is well covered at present by computer
programs and special-purpose machines. Any CX-52 traffic that appears
will tax our present facilities severely. It will require more compli-
cated, faster programs; and most of the present special-purpose equipment
will not be applicable.
The following information was extracted from the report that Friedman filed on his return to the US, on 15 March 1955. Unfortunately, much of this report has been redacted, but fortunately, there are three versions of this document, each of which has been redacted differently [18][19][20]. As a result we are able to fill-in some of the gaps and get a more complete picture. In February 2020, we were able to fill in more of the gaps, after the revelations from Operation Thesaurus — the secret purchase of Crypto AG by BND and CIA.
Friedman's visit to Zug 1955
21-28 February 1955
In late 1954, NSA director Ralph Canine advised that the Hagelin negotiations should begin again. On 17 December, the USCIB authorises a visit to Zug, where Friedman shall propose a new deal: in return for controlled sales, USCIB will authorise a statement to NATO that, if properly used, the CX-52 provides good security. USCIB hopes that this proposal will satisfy Hagelin.
More...
On 21 February 1955, Friedman arrives in Zug (Switzerland) and stays at Hagelin's home for a full week, during which time they discuss cryptographic, business and private matters. Boris Hagelin's son, Bo, will also be present during some of the meetings. During these meetings, Friedman asks about the differences between the various machine variants and about the customers that these machines are sold to. Finally, he puts the authorised proposal forward.
Move to Switzerland
At this point in time, the factory in Stockholm (Sweden) is manufacturing the current C-line of machines (C-52 and CX-52) with a capacity of 60 to 80 machines per month. Besides these machines, the Stockholm plant has also received an order for 500 to 1000 old C-446 machines. Hagelin is about to close down the factory in Sweden and move the entire production and the production facilities over to a new building in Zug (Switzerland) as soon as this is ready.
The top floor of the new building will be converted into an appartment for Sture Nyberg, the current plant manager in Stockholm, who will move to Zug with his family to become the new plant manager there. It is Hagelin's intention to let his son Boris Hagelin Jr. (Bo) take over the company when he himself retires in two years time as he reaches the age of 65.
The message that the old C-446 is to be taken into production again, plus
Hagelin's suggestion that he might want to make more, and sell them to other
countries, clearly pleases Friedman.
The interior of the C-446-A, seen from the right.
Being very similar to the M209, Friedman reports about the C-446: This model is, of course, easier to solve than the new models. Production of the C-446 machines will be completed in Sweden, even after the move to Zug is completed, where the Johannes Gauge Company has taken over the building and the workers and has been given the tools, jigs and dies on loan.
New technology
Amoung the things Friedman wants to discuss, are the capabilities of the new machines, in particular the C-52 and CX-52, and the various variants of these machines. For this, Friedman and the Hagelins agree to use specific (secret) designators, which are actually suffixes to the model name. First of all, Hagelin recognises the following two classes of C-line machines:
Class 1
Where all keywheels advance the same number of steps. In the case of the
M-209, the C-446 and a particular version of the C-52, the advance is 1
step. The machines in this class are not to be equipped for operation with
One-Time Tape (OTT).
Class 2
Where stepping is irregular and where OTT readers are provided, as well as
equipment for producing OTT tapes. These machines use the new technology.
Class 1 machines
M-209
No longer in production but still in use with the US Army and some of its
customers.
C-446
No longer in production but still in use by some countries, including The
Netherlands. Will be taken into production again for a limited period,
following an order for 500 to 1000 units by the Foreign Office and the
Department of Defense of The Netherlands.
C-52
By default, this model is compatible with the M-209 and C-446, but can also
be made to function with interchangeable key wheels and with key wheels that
have a larger number of elements (steps) than M-209 and C-446. The C-52 can
be supplied with more than 6 key wheels and may also have more slide bars
than the M-209 and C-446.
Class 2 machines
CX-52a
This model is supplied with Standard A slide bars, which produce irregular
or varying angular displacements of the key wheels, each wheel advancing 0,
1, 2, 3, 4 or 5 steps on each operation. This is the default and most secure
version of the machine.
CX-52b
This model is supplied with Standard B slide bars, which produce regular or
fixed anglular displacements of the key wheels, all advancing the same
number of steps, but the number of steps may be any one from 1 to 32. It is
weaker than the a-variant.
CX-52c
This model is compatible with the old types of C-machines, the M-209, the
C-446 and a certain version of the C-52. It is the weakest of the models.
CX-52ak
This is basicially a CX-52a that is enhanced with the so-called
Complementary feature (here written as 'Komplimentary'), also known as the
Hüttenhain 1 feature.
CX-52bk
This is a CX-52b that is enhanced with the Hüttenhain 1 feature. This
variant is built by HELL (licenced by Hagelin) for the German and Austrian
market for which HELL has an exclusive contract. It is the only version that
is approved by Dr. Erich Hüttenhain 1 for use by the German Bundeswehr
(Army), where it is known as the HELL H-54.
CX-52ck
CX-52c with Hüttenhain 1 feature.
CX-52/10
This is a 10-digit numerical-only variant of the CX-52. These machines can
be of the a, b or c type and may have the complementary feature as well. For
example: CX-52ak/10.
CX-52/30
This is a 30 character version of the CX-52, suitable for the Arabic (and
possibly Russian) alphabets. For example: CX-52/30 Arabic.
CX-52/RT
This is the Random Tape or One-Time Tape (OTT) variant of the machine.
HELL H-54 (CX-52bk) aside a CX-52ak (right)
During WWII, Dr. Erich Hüttenhain was the chief cryptologist of the Third Reich. After the war, he was employed by the new German Intelligence Agency, the Organisation Gehlen (OG), in 1956 renamed to Bundesnachrichtendienst (BND).
Customers 1955
One of the goals of Friedman's visit to Zug, is to find out what models Hagelin is selling to which customers. When asked, Hagelin gives a full rundown of his current customer base, without any hesitation, and provides details of the machines he has sold or is currently selling to them:
EgyptNegotiating for 50 x C-52 and 10 x BC-52
Jordan10 x C-52, 20 x BC-52 (UK is paying for this order)
IranNo agent, no interest
IraqNegotiating for 50 to 200 x C-52 with Arabic characters
Syria50 x C-36 1
Saudi ArabiaNo agent, no sales yet
IndiaInterested in C-52 and BC-52
PakistanWaiting for C-52 for Hindustani (29 or 30 characters)
Belgium200+ x CX-52a, 100 variable type wheels for C-446
France80 x CX-52a, 20 x CX-52a/10 (for study), interested in HX
Portugal5 x CX-52a
ItalyAwaiting NATO viewpoint on CX-52
Greece and TurkeyInterested, documentation sent. Trip postponed.
Holland500 to 1000 x C-446, some with OTT (C-446/RT)
Dutch ArmyInterest in CX-52 and BCX-52.
United Kingdom2 x CX-52
Germany and AustriaH-54 supplied by HELL (CX-52bk) 2
SwedenWill replace their C-446 by CX-52 units (long-term)
SpainInterested in C-52, no orders yet
Eire2 x CX-52
Indonesia20 to 30 x C-52 (waiting for order)
Poland and Hungary2 x C-446 each 3
JugoslaviaInterested in C-machines 4
Central AmericaNot much interest (see below)
Costa Rica2 x C-446
CubaInitially interested, but no sales
MexicoCurrently trying to raise interest
VenezuelaAbout to order some machines
Brazil60 x CX-52c, interested in 500 more
Argentine13 x CX-52c
ChileNot much interest, will buy some
PeruInterested in 200 x CX-52
ParaguayNo interest
Uruguay5 x CX-52, 2 x BC-52 (first experience with crypto)
Columbia100 x CX-52, 40 x BCX-52
Being asked by Friedman where he got the old C-36 machines from, Hagelin
replied that they had found some in the basement of the plant in Stockholm.
The CX-52bk (or HELL H-54) was the only model that was approved by Dr. Erich
Hüttenhain for use by the German Bundeswehr (Army).
The head of Swedish COMINT, Rossby, didn't think the Russians were helping their satellites with cryptographic advice or material. Friedman decided not to comment on this.
At this point, Hagelin was treating Yugoslavia the same as the Arabic countries, but Friedman suggested to treat them as a satellite of the USSR (Russia). Hagelin replied: That's OK with me if you want it that way.
Teleciphering equipment
As announced in 1950, Hagelin now produces equipment for the online/offline protection of teleprinter circuits. During the meeting, Hagelin tells Friedman that the TC-52, which has been in production for a while now, will soon be replaced by the improved TC-55. Both machines offer two types of encryption: built-in pin-wheel encryption and, as an option, One-Type Tape (OTT). The NSA is clearly worried about the availability of automatic OTT equipment to certain countries.
Pocket cipher device
Both Hagelins are very enthusiastic about the new pocket cipher device that is currently being developed. The device uses six notched discs and operates just like the C-machines, albeit without the slide bars. The cipher discs will be made of plastic and should be user-configurable. Furthermore, Hagelin Sr. hopes to be able to add a small paper strip printer to the design.
Although Hagelin Sr. gives the impression that he invented the machine himself, his son Bo tells Friedman, in a private conversation, that it was actually his idea and that it was initially rejected by his father in 1951. The idea came to mind after repeated requests from various customers for a cipher machine that would fit in a pocket.
Recently, the Swedish company Transvertex, introduced a small pocket size
cipher machine that was developed by Vigo Lindstein, a former Hagelin
employee. The machine is called HC-9 and was at this time under evaluation
at NATO.
The Transvertex HC-9, a portable cipher machine developed in Sweden by Vigo
Lindstein, a former Hagelin employee.
According to Bo, this has prompted his father to come up with a smaller device, of which he now thinks that he invented it. When Bo suggested that it was actually his idea, and that he would like to receive some royalties over it, his father had become furious, Bo tells Friedman in confidence. Patents for the new machine, that will be called CD-55, have been filed and it will soon be taken into production. Various models are being considered, including one, if possible, with OTT.
Siemens and Halske
Many other interesting points are raised during the various meetings between Friedman and Hagelin on this visit, such as the modification of the B-211 for the French, and the production of HX and CX machines by the private French company Societé Electronique Automatisme (SEA).
Another point that is raised, is the current situation with Siemens and Halske. Although the German Siemens company clearly is a competitor of Hagelin, there are strong connections and there have been frequent exchanges of information between the two companies, some of which in relation to the work of Dr. Erich Hüttenhain, the former Cryptologist of the Third Reich who now works for the German Intelligence Service, the Bundesnachrichtendienst (BND).
At several moments in history, Hagelin contemplated selling his company to Siemens, but this never happened. In the talks with Friedman, Hagelin mentions that the relations with Siemens and Halske are now formalised in a signed contract. As a result, Siemens will not make any cryptomachines themselves and Hagelin will refrain from producing teleprinter machines. In this contract, the market for teleciphering machines is divided as follows:
Siemens alone
West Germany
West Austria
Jugoslavia
Portugal
Ireland
America (all except Brazil, USA and Canada)
Africa (all except Egypt)
Asia (all except India, Indonesia and China)
Australia
Crypto AG alone
France
Italy
Switzerland
Sweden
Norway
Benelux 1
Brazil
Egypt
India
Siemens and Grypto AG together
Denmark
Greece
Spain
Indonesia
Areas not yet agreed
Finland
Russia and all satellites
East Germany
China
USA and Canada
Benelux is the abbreviation for Belgium, Netherlands and Luxemburg.
The Hagelin Deal 1955
After having been Hagelin's guest for several days, on the evening of 25 February, Friedman feels the time has come to place the NSA proposal before Hagelin, or, as he puts it in his report: the real object of my visit to Zug. He begins by thanking Hagelin for his patience and for keeping his part of the Gentleman's Agreement, despite the fact that the NSA has exceeded the deadline.
The NSA had been struggling for more than twelve months, rather than the anticipated six, to work out a proposal that would be satisfactory for them (the NSA) as well as perhaps acceptable to Hagelin. They had hit upon a simple one that he was now authorised to put before Hagelin.
Hagelin replies by thanking Friedman for the appreciation and understanding of his position and for various favours that were done for him and his family, in particular for his son-in-law Conradi and for his wife's cousin Miss Barth, who had been given a position at the NSA or the US Army.
Friedman then conveyed to him practically verbatim the terms of the proposal authorised in USCIB: 29.14/29 of 27 December 1954. He tells Hagelin that he does not have to decide right away, and that he can take some time to think it over, but to his great surprise, Hagelin accepted the proposal then and there, without any reservations or desire for modifications.
When Friedman offers him to ask DIRNSA to confirm the deal in a formal letter, Hagelin replies that he doesn't want anything with respect to this deal on paper. Although the contents of the proposal authorized in USCIB: 29.14/29 are still classified, we now know the details:
From 28 February 1955 onwards, the agreement between NSA and Hagelin is
official
The deal is secret and is for an undefined term (no end-date)
Hagelin will refrain from selling to proscribed countries 1
Hagelin will not be payed for this
Hagelin will continue to supply information to the NSA,
NSA will write the brochures and manuals for the CX-52 models [21]. 2
NSA will approve CX-52 for NATO (if properly used)
NSA will write the 'proper usage' manual for for NATO. 3
Further to this we can make a few 'educated guesses':
Hagelin will continue to receive personal favours for him and his family.
Hagelin will be able to buy back several lots of M-209 machines.
Bo Hagelin Jr. has asked for a TYPEX machine which Friedman hopes to find
for him.
The US Army will place a large order for C-52 and CX-52 machines.
Hagelin will not sell secure machines (like CX-52 and OTT machines) to
countries on this list.
These manuals were written by Dr. Harold J. Stukey and Francis A. Raven of
the NSA [16].
In order to make best use of their machines, Hagelin usually released a
manual for 'proper usage'. For the machines used by NATO, it was agreed that
the NSA would write this manual. This could imply that Hagelin received NATO
orders as part of the deal with the NSA, but this can not be confirmed at
present.
CX-52 Manuals
In the past, Hagelin has noticed that some of their customers are not using their cipher machine to the best of its abilities. For example: the configurable pins on the cipher wheels and the lugs on the sliding bars can be set up in such a way that the cipher period 1 is shortened. In order to avoid such situations, Hagelin has issued a manual for 'proper usage' for each of his machines.
One of the outcomes of the Hagelin Deal, is that the NSA will provide the manual for 'proper usage' of the CX-52. The manual will be written by Dr. Harold Stukey and Francis A. Raven, two high ranking cryptologists at the NSA. Although this can be seen as a gesture of courtesy on behalf of the NSA, it is far more likely that it was used by the NSA to weaken the cipher by manipulating the instructions for best use. It takes the NSA seveal months to complete the manual, during which time Friedman regularly keeps Hagelin informed about the progress.
During the meeting, Hagelin is clearly worried about the proper use of his machines by NATO. He asks Friedman how he can assure that NATO uses the devices properly. Friedman answers that he does not need to worry and that the NSA will take care of that too. This means that the NSA will also write the instructions for best use for NATO. This fits in with the NSA's desire of the 1950s to improve the overall cipher security of their NATO partners, in particular that of France. 2
In cryptography, the cipher period is the time it takes for the key stream to repeat itself.
At this time, France is known to use weak cipher systems and/or use their stronger cipher systems in an improper manner, as a result of which many NATO secrets have leaked to the USSR (Russia). Various memos in the Friedman Archive confirm that the NSA is determined to fix this leak.
Bo the spy
It is worth noting, that during Friedman's visit he becomes aware of problems in the relationship between father Boris and son Bo. He makes two remarks: (1) Bo has acquired the exclusive sales rights of the new portable CD-55 cipher machine, and (2) Bo offers to provide copies of internal correspondence (i.e. spy), if that would help to cement the relationship with the Americans.
The first remark (CD-55) would eventually get in the way of a smooth relationship with the Americans, who regarded Bo Hagelin as an unguided missile, more inclined than his father to sell to the highest bidder, rather than to a friendly country [27].
Friedman's retirement 1955
On his return from Zug on 3 April 1955, Friedman suffers a heart attack and is hospitalised, which delays the implementation of some of the points of the agreement. After he is discharged from the hospital, Friedman works from his home for a while and writes to Hagelin several times.
Later that year, in August 1955, Friedman officially retires from the NSA but will remain working for the agency as a consultant. Due to his bad health - he has a serious heart condition - he is unable to handle Hagelin, so the NSA sends Dr. Lawrence (Larry) Shinn in his place while Bill Friedman takes a step back. He would later be replaced by Howard Barlow.
Down the drain
The Hagelin deal had imploded the moment Friedman entered the hospital. The first problem was the deal that NSA would write the manual for proper use for NATO. The organisation strongly objected and refused to do so. On 24 May Canine expresses Friedman's and his own dismay. But to no avail. NSA disliked the USCIB agreement and Sinn wrote a letter to Hagelin to demand that he stop informing potential customers that NATO approval was forthcoming. Clearly, it was not.
NATO would be implementing AFSAM-7 and not some mechanical Hagelin machine. Sales of CX-machines to NATO countries would eventually dry up. Another problem was the list of proscribed countries. The COMINT department of NSA protested, as this was actually a list of targets, which NSA was very reluctant to share with anyone, let alone an uncleared foreigner. In late 1955, Sinn was ordered to visit Hagelin in an attempt to repair the broken relationship. He appologised for NSA's inability to keep their part of the bargain, and – surprisingly – Hagelin accepted.
During Sinn's visit, Hagelin was asked about sales of CX-machines to Egypt, that had been brought to the NSA's attention, but Hagelin said he knew nothing about that.
Bo's move to the US 1956
Although Hagelin initially wanted to let his son, Bo, take over control of the company after his planned retirement in 1957, he has his doubts about the competence of his son and feels it would be better to let him run his own business for a while. He suggests that Bo should handle the Latin American crypto market, before taking over the company completely. Bo, meanwhile married to his American wife Edith, moves to Washington and sets up his own business there.
Friedman's visit to Zug 1957
22 September 1957
Broken promises
Dr. Lawrence Shinn, who replaced Friedman after his retirement, would only last through 1955. After a couple of visits to Hagelin, in which he tried to repair the broken relationship, he was replaced in 1956 by Howard Barlow, an NSA COMSEC engineer who had previously travelled Europe together with Friedman, to check out crypto firms. Like Sinn, Barlow would not last.
It was clear that Hagelin was not happy. The Americans were not promoting the CX-machines to NATO (on the contrary), surplus M-209 machines were still 'leaking' onto the market, his main competitor Siemens was selling to countries that Hagelin was not allowed to sell to, and French intelligence people had rumoured that the Americans and British services disliked Hagelin.
Sales of CX-machines to denied countries in 1957
In the meantime, the new CX-machines were piling up in his warehouse. In early 1956, Hagelin began to covertly sell them to denied countries. By late 1957 he had sold 347 machines to Asian and Middle East countries. In addition, he had started selling to Latin American countries, but since the US did not want to admit that it targeted those countries, there was nothing to be done.
Friedman returns
Then in the summer of 1957, during a planned visit of Barlow to the factories in Stockholm and Zug, Hagelin specifically asks for Friedman to meet him in Zug in order to continue the talks with regard to the Gentleman's Agreement, and to see the latest developments. Friedman is recalled from retirement and arrives in Zug on 22 September 1957, authorised to modify the agreement. He stays at Hagelin's home for a week, during which time a variety of subjects are touched.
During this week, Hagelin himself briefly travels to Paris for a meeting with the French Army, where he gets a large order for cipher machines. On his return he reports his dealings with the French to Friedman. Whilst Hagelin is away, Friedman visits the factory and laboratories and is shown the latest developments by manager Sture Nyberg and chief developer Oskar Stürzinger.
Hagelin and Friedman talk at great length on a variety of subjects, customers and competitors. Friedman seems to be very interested in what Siemens are currently doing with respect to their online OTT systems and how they are dealing with the problem of radiation (TEMPEST).
Re-injection patent
The first thing to be discussed between Hagelin and Friedman, is patent 2,802,047 that Hagelin has filed in the US in October 1953 and that had been granted just last month. Although it was granted in the US, the patent was declined in Japan. Hagelin wonders why that would be the case.
The patent describes a cipher machine in which more contacts are used on the cipher wheels than are actually needed and where the extra contacts of the output of the drum are looped back to the input. This method can be described as re-entry or re-injection and will be used in Hagelin's new HX-machine which is underway.
Friedman was shocked when he saw the patent, but didn't say that to Hagelin. The principle of re-injection was registered by the US around 1940 in a secret patent, so Hagelin's attempt should have raised a declaration of interference.
The re-entry principle was conceived during WWII by Albert Small, whilst working for the Army Signal Intelligence Service (ASIS), trying to solve the high-level Japanese diplomatic Purple cipher. It is covered by US Patent 2,984,700 and has since been used at the heart of the high-level American cipher machine AFSAM-7 (later: KL-7) shown above, that was also adopted by NATO.
Although officially Hagelin should not be aware of the existence of the AFSAM-7, in later talks he mentions that many of its operators are experiencing contact problems with the rotors. 1 This proves that Hagelin was well aware of the existence of the machine and that he might have been aware of the re-injection principle being used in it. He also explains how he conceived the idea after a trip to Bonn in 1952, were he was told something 2 by Dr. Huttenhain, followed by discussions with his chief developer Oskar Stürzinger, but stresses that it was his own idea.
More about the KL-7
This is actually correct; the KL-7 was known for its many contact problems
if the maintenance instruction were not strictly followed.
It is currently unclear as to what Hüttenhain told Hagelin on this occasion,
or what Hagelin discussed with Stürzinger afterwards, as the original
document is redacted at this point. It is entirely possible though, that
Hüttenhain was talking about the AFSAM-7. The same principle was later also
used in the Russian Fialka.
Problems with Bo
From his arrival on the 22nd, it had been clear to Friedman that there were problems between Boris Hagelin Sr. and his son Bo. Since arriving in the US, where he is now handling the sales of cipher machines to the Latin American countries, Bo had been spending too much money (privately) and has even asked Boris for US$ 25,000 as an advance payment on his inheritance.
After sending the US$ 25,000 plus another US$ 5,000 to Washington, Hagelin, irritated by his son's financial conduct, said that no more money was to be sent to him. According to Boris and his wife Annie, the problems were largely due to compatibility issues with Bo's American wife Edith. Dr. Hell, who had visited Bo in the Spring of 1956, had reported that Bo was homesick for Switzerland and wanted to return to Europe, but that his wife had opposed to this idea.
Hagelin confines to Friedman that he had contemplated merging his business with Siemens as he is tired of being the only whipping boy. Once merged with Siemens, they could take over the handicaps imposed by limitations and restrictions as to whom I can sell what machines, Hagelin says. Friedman asks whether he has thought of merging his business with Hell, but Hagelin rejects that idea, as Hell is in a different kind of business, whilst Siemens would be more suitable.
Unknown to his son Bo at this point, is Hagelin's decision to finally move the activities from the Stockholm factory fully over to Zug, as he wants all developments and operations in a single place. If they want to do so, the Stockholm employees are allowed to move to Zug as well. Although Hagelin initially wanted to handover management of the company to Bo, he doesn't see that happening in the nearby future, and thinks that he has to stay on for a number of years.
Friedman also seems to have trouble with Bo, as he reports to Hagelin that Bo is currently visiting every legislation and embassy in Washington in order to 'educate' them with instructional literature about proper usage of the equipment. There was one document in particular that bothered the NSA and Friedman asks Hagelin what he can do about it. Hagelin answers that, with Bo being a citizen of the United States, the NSA is in a far better position to handle the issue.
OTT machines
Friedman and Hagelin have long discussions about Siemens and their use of OTT equipment. Hagelin has heard that Siemens was about to sell OTT equipment to a country behind the Iron Curtain, and he wanted to find out whether this was true. It is then that he learned that the German Government had given Siemens the green light to sell their OTT equipment, including suitable OTT generators, the every country in the world, except for the USSR and its satellites.
Hagelin thinks that his company will follow suit. Siemens is currently developing an OTT key tape generator designed by Hüttenhain for the German Government, but for other customers they will order the key tape generators from Hagelin. Alternative generators are currently being developed at Lorenz, Olivetti and OMI. 1
Hagelin has developed OTT extensions for most of their existing cipher machines. This means that the cipher units of machines such as the C-446, the C-52 and the CX-52 can be removed and replaced by a drop-in OTT mechanism.
Friedman is clearly impressed with the mechanical quality of the OTT assemblies and the relative ease with which they can be installed. He thinks that they could be suitable for NATO countries and their allies. Asking again about Siemens, Hagelin reveals that they have already sold OTT equipment to Yugoslavia and probably also to Egypt and India. It would later turn out that on a recent trip to Yugoslavia, Mr. Nyberg had made a relative large sale for Hagelin as well.
Is is currently unknown what type of key tape generator was being developed by Dr. Hüttenhain (as this is redacted). Apparently neither Hagelin nor Friedman are aware that Willi Reichert is meanwhile developing the only true random generator for OTT production, the so-called 'Würfel' (dice).
Three categories
Something that was completely new to Friedman and that he had not heard from Hagelin in any of his earlier conversations or letters, was the fact that Crypto AG now produces three different versions of each of their machines. Hagelin himself had initially thought that two categories would have been sufficient, but after talking with NATO people, Nyberg and Stürzinger had decided that three would be better. The three types or categories are:
Best security
Machines for the West or West-oriented countries, including NATO members and
NATO-friendly countries. These machines will be the best Crypto AG can
produce. They will offer the maximum flexibility with regards to usage, and
will have OTT capability where appropriate. These machines will also be
properly shielded against unwanted radiation (TEMPEST) and will be supplied
with instructions for proper usage.
Medium security
Machines for the friendly neutral countries. These machines are not as flexible as the Type I machines. Countries belonging to this category have not yet been determined, but Finland, Switzerland and Pakistan are suggested.
Low security
These machines offer the lowest quality and flexibility. They will have a
simpler keying mechanism and can not be equipped with an OTT option. The
Middle East, Asia, USSR and satellites fall into this category, as do
Indonesia, India and Egypt.
Lacking NSA cooperation with respect to writing the manuals, Hagelin reports
that he has done it himself. The brochures, instruction manuals and
guidelines for proper usage will be different for each category and will
have 'secret marks' to make them distinguishable. According to Hagelin it
will be difficult, but necessary, to maintain records of what version each
country is using.
The pocket devices
The pocket cipher devices, that Hagelin had talked about on their previous
meeting in 1955, are now ready and in production. There appear to be two
different versions, the CD-55 and CD-57, that are cosmetically identical, in
other words: the average user will not be able to tell them apart.
The CD-55 will be available to all customers in all countries, and will be
housed in a green case. It's operation is similar to that of the C-38, the
C-446 and the M-209 and the machine will therefore be easy to break or solve
by the NSA.
The second variant is the CD-57 that is built around the new keying
mechanism, similar to the one used in the CX-52, although from the outside
this is not visible. In addition, the CD-57 can be converted into an OTT
machine quite easily, by removing the keying mechanism and replacing it with
a drop-in OTT assembly.
The CD-57 is housed in a grey case 1 and will only be sold to NATO and NATO-friendly countries. Although it was intially planned to have a small built-in printer, this was dropped in the final version. Instead, the operator now reads the output from an revolving alphabet disc at the front. Furthermore, the cipher discs are now made of aluminium rather than plastic. According to Boris Hagelin Sr., the small CD machine will be suitable for secret agencies and small army units.
According to Hagelin, the CD-55 is housed in a green case, whilst the CD-57 is grey. He probably refers to the colour of the Hamerite paint here. For NATO, the CD-57 was also avaialable in NATO olive green.
Willi Reichert
Before Friedman arrived in Zug, he had made a brief stop in Frankfurt where he was brought up to speed by his colleagues at NSAEUR and ASAE. On this occasion they informed him about a certain Willi Reichert, who is selling surplus WWII Siemens Geheimschreiber machines (also known as T-52, Tunny and Sturgeon) to the French. He asks Hagelin whether he knows Willi Reichert.
Hagelin says that he doesn't know him personally, but that he doesn't think very high of him as, according to him, he sells to both sides. Hagelin thinks that Reichert has some kind of 'secret cache' from which he gets the old machines and parts, but that his supply is about to run out.
It is unknown why the NSA was interested in Willi Reichert, but it must have been around this time, that Reichert had obtained a patent for a noise generator, from Dr. Werner Liebknecht at Lorenz. Reichert needed it to build a true random number generator for the creation of OTT tapes for the German Government in Bonn. Reichert built a successful business from this and would later move his company to neutral Austria, where it still existed in 2018 as Mils Electronic.
TEMPEST
Siemens engineers had recently discovered that radiation from a cipher machine (both acoustic and electromagnetic) can lead to unwanted leaking of information. In some cases it had turned out to be possible to recover most of the plaintext from an intercepted signal, in particular when using landlines for transmission. During his short stay in Frankfurt, Friedman had been informed about this and he is now trying to find out how much Hagelin knows about this subject.
Hagelin seems to be well-informed as he tells Friedman pretty much the same as what he had learned in Frankfurt. Like Siemens, Hagelin is now taking the necessary precautions to shield his machines against such radiation. According the Hagelin, the French are also aware of this problem, but do not take it very seriously. For Friedman this confirms the French situation. 1
Although Friedman acts as if this whole radiation issue is new, he must have been familiar with it, as the effect had been known at the NSA for quite some time, and had certainly been exploited by them. Unintended leaking of information, or unwanted emanations, is also known as TEMPEST.
For a number of years, high-level NATO information has been leaking to the USSR (Russia) due to insufficient cipher security by the French (see also above).
Visit to France
Whilst Friedman is his house guest, Hagelin has to leave him for a couple of days for a scheduled meeting with the French Interdepartmental Committee on Cryptography in Paris. On his return, sooner than expected, he gives Friedman an account of his business with the French Government and tells him that he has just got an order for about US$ 250,000 for CX and TC machines. The machines were intended for use by the French Army, the Air Force and the Foreign Office.
Whilst in Paris, he briefly discussed his Gentleman's Agreement with the French, who told him that they too would be very happy if he would refrain from selling certain machines to certain countries, but that they had no legal means of forcing him to do so. Despite this, they give him substantial orders for equipment, not just one or two as does the US, Hagelin jokingly adds.
Barlow's visit
Friedman's intervention was clearly appreciated by Hagelin, and the relationship with Howard Barlow – his new NSA contact – improves. In November 1957, Barlow visits Zug again to speak with Hagelin and they part as good friends. On his return in Washington, barlow reports that he thinks that Hagelin is also pressed with sales restrictions by the French and Swedes. His is certain of Hagelin's loyalty towards the Americans however, as he is well aware of the M-209 threat.
The aftermath 1958-1993
In the following years, Friedman's health deteriorates and he is in and out of the hospital. As a result, he will not be able to visit Hagelin in Europe in the foreseable future and does most of his work from the study in his home. Financial (tax) issues prevent him from travelling on his own expense and the agency wouldn't permit him to visit Hagelin anyway, he writes in 1961.
In 1962, Friedman picks up a consultancy job at RCA and starts thinking about leaving his collection to some organisation. After Princeton University turns down his offering, he decides to come over to Zug (Switzerland) and work with Boris Hagelin on writing the latter's biography. He even contemplates moving to Europe permanently, but this never happens. He loves the US more.
On his return to the US, Friedman will work out the notes and tape transcripts of Hagelin's biography, but recurring health problems prevent him from doing so. In spring 1966, Hagelin's wife Annie doesn't feel well and after a short illness she dies on 29 November 1966, just after she and Boris had moved into their new appartment in Minusio (Switzerland) a month earlier.
In 1967, Friedman has found the Marshall Foundation willing to accept The Friedman Collection and look after it. In September 1967, Elizabeth Friedman writes that Bill now has dayly visits from a typist of the foundation, who is taking down his oral history. Bill is too weak to write or type himself but he is feeling better now. She also writes that Bo is having troubles with his wife Edith, and that Bill is being plagued by newly released books from David Kahn and Farago. Apparently both men have approached Friedman several times and he has difficulty fighting them off.
In May 1968, Hagelin plans a trip to the US and is invited to Friedman's home again. He wants to talk about the activities in Zug and about new technologies, such as integrated circuits that they are now beginning to use in their devices. Unfortunately, on his arrival on 8 October, Friedman had just suffered another heart attack, so they have to meet in the hospital in Washington.
Over the past 10 years, the relationship between Boris and his son Bo has not been too well, to put it mildly. Although they do write to each other occasionally, and no longer fight over the CD-57 patent issue, they each do their business in their own part of the hemisphere. Friedman on the other hand, has built quite a good relationship with Bo in recent years and sees him regularly.
In March 1969, Friedman's health has improved to the point were he writes a long letter to Hagelin in which he comments that Bo mentioned recently that he hadn't seen his father in the past 5 or 6 years, whilst he (Bill) had seen him at least three times in the recent past. He hopes the two will see each other again soon and spend some time together. A month later, he returns the hand-written biography of Hagelin to Zug, as he has no energy left to finish it. He hopes Boris will find a good biographer to complete it. In November 1969, Friedman dies at the age of 78.
Sadly, Bo dies the next year in a fatal car accident and soon after that, Boris Sr. resigns from the board of Crypto AG and finishes his memoirs a few years later in 1979, first in German [2] and then in 1981 in the English language [3]. By the time he dies on 7 September 1983 – aged 91 – he leaves behind a healty company with customers in over 130 countries. He leaves us a legacy of beautifully crafted mechanical cipher machines, but he also leaves Crypto AG his clouded past.
Der Fall Hans Bühler 1992
In 1992, Hans Bühler, a top sales representative of Crypto AG is arrested in Iran on the suspicion that the Hagelin cipher machines used by the Iranian Government are flawed, or in more popular terminology: that they contain a backdoor. A loose remark of US President Ronald Reagan about evidence against Libya had led them to believe that Crypto AG was cooperating with the US.
Bühler, who is fully unaware of any manipulation with the machines, is interrogated three times a day for nine months and is finally released in 1993, after the bail of US$ 1,000,000 is payed by Crypto AG. This incident is certainly not the finest period in the history of Crypto AG.
Immediately after Bühler's release from prison and his subsequent return to Switzerland, he is fired and, in addition to that, the company also wishes him to repay the US$ 1,000,000. Bühler then decides to go public and confines his story to a book that is published in 1994 [22].
The Swiss Federal Police, the Bundesanwaltschaft, has investigated the matter and questioned several people, and it is said that no irrefutable evidence against Crypto AG was ever found. The outcome of the investigation however, remains classified to this day and repeated requests from journalists for public disclosure of the results of the investigation have been denied so far.
Since Hans Bühler went public, some of his former colleagues have decided to come out as well. Former software engineer Jürg Spörndli confirms that the company was visited frequenty by NSA specialists and that on several occasions he was instructed by his manager to swap a cryptographic algorithm that he had developed, for an alternative one that was clearly weaker [23].
In 2008, Crypto Museum had the priviledge to have a private talk with Oskar Stürzinger, former chief engineer at Crypto AG and first employee of Boris Hagelin when he established his company in Switzerland [24]. When asked about the case of Hans Bühler, he confirmed that the company had frequent visits from NSA people who had meetings with software engineers and that on some occasions he wasn't even allowed to be present in the room. He said it made him feel uneasy.
Stürzinger also confirmed that since the Bühler case had become publicly known, there have been governmental investigations. As a result, the current management of Crypto AG had taken the necessary measures to ensure that this should never happen again. He was confident about that.
Conclusions
From the evidence found in the documents from the Friedman Archives [1], that were (partly) released by the NSA in 2014, it has become certain that some kind of agreement existed between the NSA and Hagelin as early as 1951 and that this agreement was reviewed and/or renewed several times, in any case in 1955 and in 1957. This agreement was never confined to paper and did not have a termination date, and it is likely that it continued after Hagelin's death in 1983.
In closing, we feel that we should say a few words in Hagelin's defense. Given the fact that he had a very good relationship with the Americans — in particular with Bill Friedman — and that they brought him his initial fortune by allowing him to supply cipher machines to the US Army during WWII, it seems only natural that he remained loyal to his old friends. From the correspondence between him and Friedman, we get the impression that he was a man of his word, and that he did what he did with the best intentions with respect to safety in Europe and in the rest of the world.
The above story is the result of extensive research in the Friedman Collection of Official Papers by the British Broadcasting Corporation (BBC) and Crypto Museum in July 2015. It was the subject of a radio program that was aired on 28 July 2015 on BBC Radio 4 [25]. In an official reaction to the BBC, Crypto AG said that, whatever happened in the past, this is certainly not happening today, and that mechanisms have been put in place, to prevent this from happening in the future.
In 2020 however, the German TV station ZDF revealed that since 1970, the company was jointly owned by the German BND and the American CIA, and since 1994 exclusively by the CIA [27]. It means that for many years, Western intelligence services were able to manipulate the algorithms of Crypto AG's products and read the communications of many of its customers. Although the company also sold unreadable 1 equipment, the list of countries that were given access to such technology became shorter every year. According to the NSA, all encryption should be readable.
![]()
![]()
![]() From FVEY to 14 Eyes - The World Takeover of the NSA
From FVEY to 14 Eyes - The World Takeover of the NSA
September 27, 2019 - Source Electrospaces.net
https://electrospaces.blogspot.com/2019/09/from-9-eyes-to-14-eyes-afghanistan.html
September 22, 2019
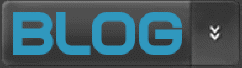
From 9-Eyes to 14-Eyes: the Afghanistan SIGINT Coalition (AFSC)
For over five years it was a mystery: the 9-Eyes intelligence cooperation, which was first revealed by The Guardian in November 2013. It was only an extensive new piece on the website The Intercept from last May that made clear that the 9-Eyes is actually the Afghanistan SIGINT Coalition (AFSC).
The main purpose of the AFSC was to collect GSM metadata using DRT interception devices and feeding them into the NSA's huge data analysis platform for Afghanistan operations called the Real Time Regional Gateway (RT-RG).
The AFSC started in 2009 with nine members but eventually grew to the same 14 countries that already cooperated in another intelligence exchange group called SIGINT Seniors Europe (SSEUR). The AFSC existed at least until the end of 2014.
Slide from an NSA presentation about the Afghanistan SIGINT Coalition (June 2009)
Intelligence sharing coalitions
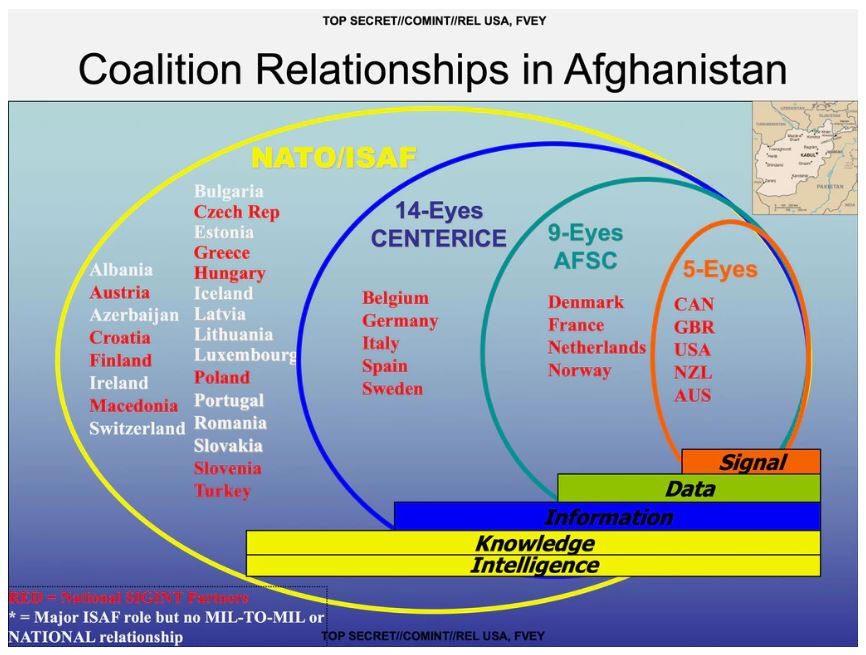
The existance of the 9-Eyes group was first revealed by the British newspaper The Guardian on November 2, 2013:
"The NSA operates in close co-operation with four other English-speaking countries - the UK, Canada, Australia and New Zealand - sharing raw intelligence, funding, technical systems and personnel. Their top level collective is known as the '5-Eyes'.
Beyond that, the NSA has other coalitions, although intelligence-sharing is more restricted for the additional partners: the 9-Eyes, which adds Denmark, France, the Netherlands and Norway; the 14-Eyes, including Germany, Belgium, Italy, Spain and Sweden; and 41-Eyes, adding in others in the allied coalition in Afghanistan."
This revelation caused some embarrassment, as especially France and The Netherlands had clearly expressed their anger about the NSA's alleged eavesdropping operations against their citizens (see below), but now it turned out they were also engaged in some close alliances with the Americans.
Other 9-Eyes: CFBLNet
The Guardian's revelation started speculation about the differences between these groups and their specific purposes. From open sources, a range of similar "Eyes" for sharing military and intelligence information were identified on this weblog in November 2013 in a posting titled Five Eyes, 9-Eyes and many more.
It turned out that the term 9-Eyes was already used since 2008 for exchanging classified information among the Five Eyes and nine NATO members of the Combined Federated Battle Laboratories Network (CFBLNet). This is a multilateral network for research, development and testing on C4ISR systems.
However, the members of the CFBLNet 9-Eyes were not fully identical with those in the Guardian article, so it seemed not likely that this was the mysterious 9-Eyes group mentioned in the Omidyar documents.

The 9-Eyes of the CFBLNet listed in a NATO standardization document from 2010
14-Eyes: SSEUR
In December 2013, Swedish television published a range of NSA-documents from the Snowden files which revealed that the 14-Eyes were also known as the SIGINT Seniors Europe (SSEUR) and consisted of the Five Eyes plus nine European partners: Belgium, Denmark, France, Germany, Italy, the Netherlands, Norway, Spain and Sweden:

From various other sources it became clear that the SIGINT Seniors Europe is a group in which the heads of the participating military or signals intelligence agencies coordinate the exchange of military intelligence according to the needs of each member.
The SSEUR group was established in 1982 for more efficiently monitoring the Soviet Union* and a database system called SIGDASYS was set up so the participating agencies could exchange as much military SIGINT and other information as possible.* In the early 2000s, a sub-group for counter-terrorism was formed under the name SIGINT Seniors Europe Counter Terrorism coalition (SISECT).
Afghanistan
Meanwhile, the function of the 9-Eyes remained unclear: the Dutch interior minister Ronald Plasterk refused to say anything about it, but there were rumours that it was for exchanging military signals intelligence related to operations in Afghanistan.
That could explain why no other documents about the 9-Eyes had been published, because apparently Glenn Greenwald had an agreement with Snowden not to disclose information that could endanger American troops in Afghanistan.
Nonetheless, information about NSA's involvement in Afghanistan did came out: in June 2014 for example, the German magazine Der Spiegel released an NSA paper from January 2013, which lists all the members of the Afghanistan SIGINT Coalition (AFSC). Its membership appeared identical with the SIGINT Seniors Europe or 14-Eyes.
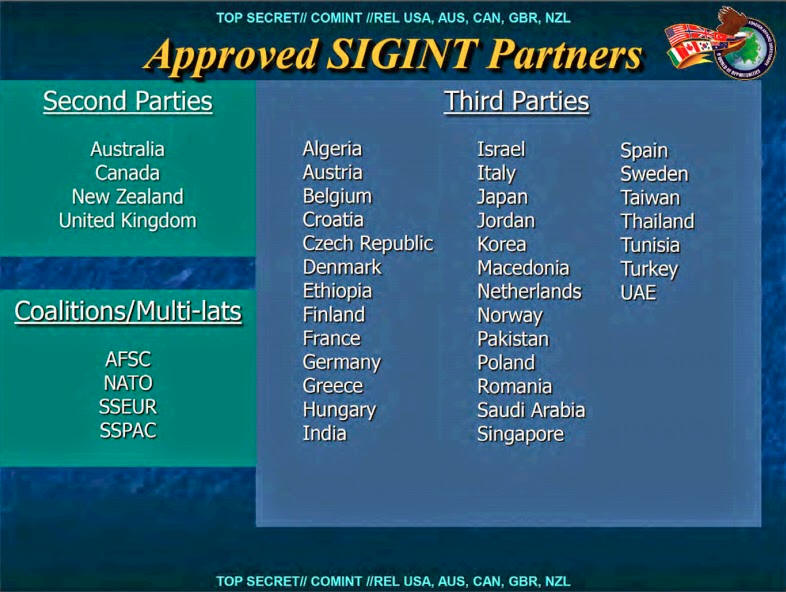
NSA presentation slide showing the 2nd and 3rd Party partners and some coalition and multilateral exchange groups. Published in No Place To Hide, May 2014.
From 9-Eyes to 14-Eyes
But as was revealed in The Intercept's article from last May, the Afghanistan SIGINT Coalition not always had 14 members: the group started in 2009 with just nine members and was therefore called 9-Eyes. Besides the Five Eyes it included Denmark, France, the Netherlands and Norway.
In 2010, Sweden and Germany joined the Afghanistan SIGINT Coalition and by January 2013, Belgium, Italy, and Spain had also become members of the group. By then, the AFSC had exactly the same membership as the SIGINT Seniors Europe or 14-Eyes.
It is not known whether the number of "Eyes" increased with each new AFSC member, but it's clear that an "Eyes" designation is not always a unique designator and there can be multiple groups with the same number of Eyes at the same time. To avoid confusion, such multilateral partnerships can best be called by their actual names.

The Real Time Regional Gateway
The Afghanistan SIGINT Coalition was created because the NSA needed additional linguistic capabilities as well as data from regions in Afghanistan where they had little or no coverage themselves.
Therefore they turned to trusted coalition partners and provided them with wireless interception equipment known as DRT-boxes, which were first identified as such on this weblog in November 2013.
After Dutch, Danish, Norwegian, German and Spanish troops each got one, two or three DRT devices, they started feeding intercepted GSM metadata into a huge distribution and analysis system called Real Time Regional Gateway (RT-RG) as of Summer 2008.
This RT-RG system was first publicly mentioned in a Defense News article from October 2010 and in the book Top Secret America from 2011 it was described as follows:
"RTRG allows users to see all signal intelligence that collectors are working on in real time. This includes ground collectors, Air Force RC-135 Rivet Joint and Liberty planes, SIGINT-equipped drones, and SIGINT satellites operated by the NRO. RTRG has provided a tenfold increase in the speed with which intercepts are povided to operators on the ground."
This is already a pretty accurate description, except that it doesn't mention the participation of coalition partners, which governments always handle as something extremely sensitive.
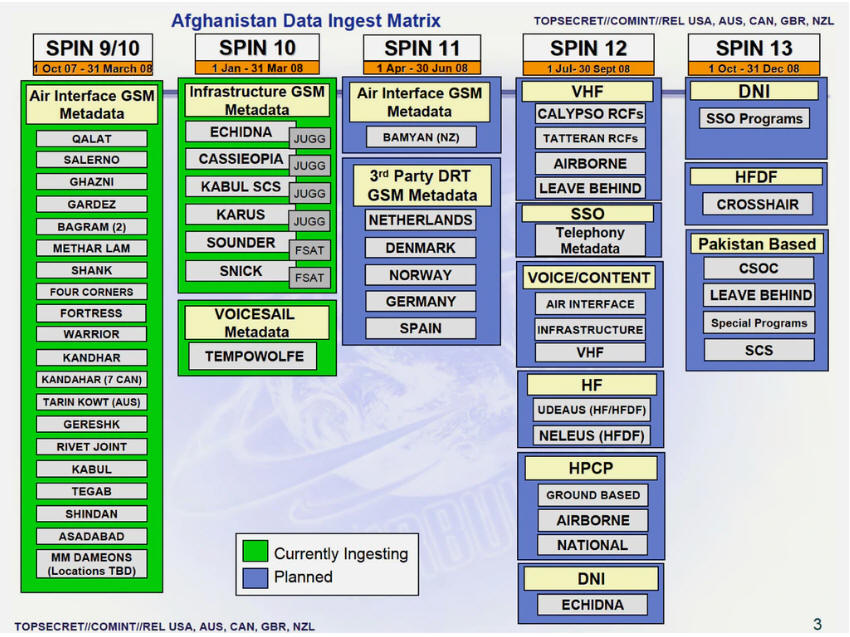
Slide from an NSA presentation showing all the collection systems that fed the RT-RG platform
RT-RG started as a project called RT-10, which was first deployed in Baghdad in 2007. An internal NSA newsletter says that in order to provide a comprehensive real-time view of the telephone and internet communications in Baghdad (with roughly 4 to 5 million residents), the RT-10 system had to be able to ingest each day:
- 100 million telephone metadata records
- 1 million pieces of telephone content
- 100 million internet metadata records
The success of the RT-RG system lay in the fact that these massive amounts of data were stored locally: in 2009, a large RT-RG data center was built at Area 82 of Bagram Airport north of Kabul. It was right next to the Afghanistan Regional Operations Cryptologic Center (A-ROCC), where analysts from the 9-Eyes countries worked side-by-side.
Previously, war-fighters in the field had to retrieve their intelligence from central databases at NSA headquarters. This costed time and bandwith, but it also meant that only data related to known targets was sent back and stored. But with storing the full-take collection in a regional repository, all data could be subjected to analytic algorithms in order to find new targets for the so-called Find, Fix, Finish operations.
In 2011, the Afghanistan RT-RG had a database of 27 terabytes, which could only store approximately one month of regional data (90% of the user queries were within a one-week timeframe though). A planned move to NSA's new cloud architecture would increase the storage space to up to 125 TB and would allow larger-scale analytics to be conducted.
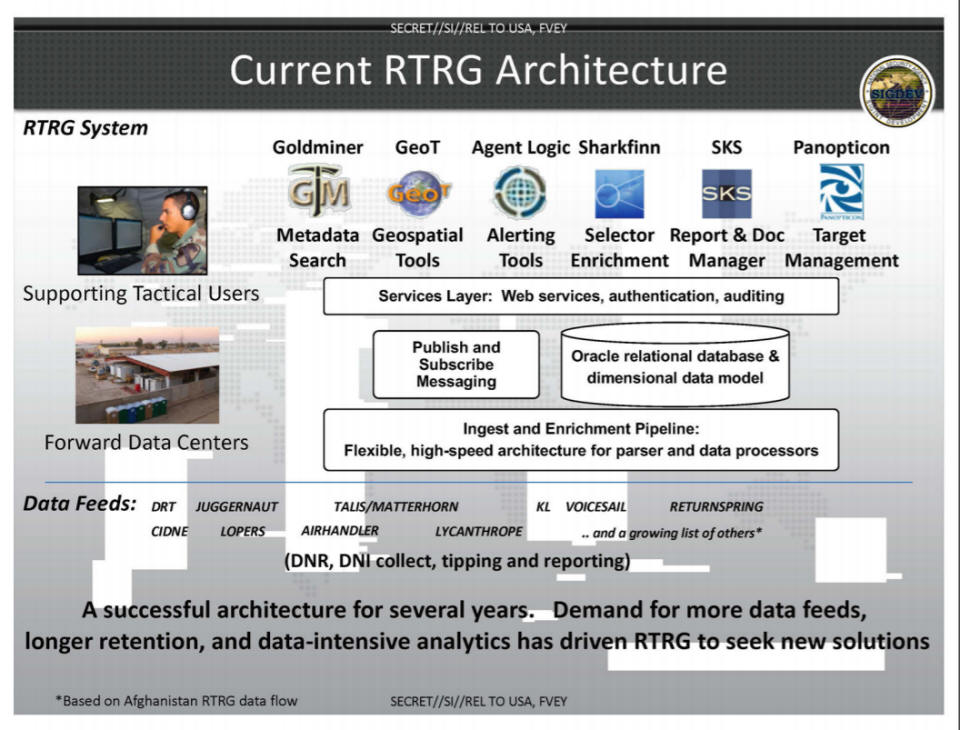
Architecture of the Real Time Regional Gateway (RT-RG) in 2012 (source: NSA presentation)
BOUNDLESSINFORMANT
How many GSM metadata the countries from the Afghanistan SIGINT Coalition collected can be seen in charts from the NSA's data visualization tool BOUNDLESSINFORMANT. The available charts show that the following numbers were acquired through the DRTBOX system during a one month period between December 10, 2012 and January 8, 2013:
- France: 62 million metadata records
- Spain: 60 million metadata records
- Italy: 45 million metadata records
- Sweden: 33 million metadata records
- Norway: 33 million metadata records
- Denmark: 22 million metadata records
(The chart for the Netherlands shows the CERF CALL method through which cellphone metadata from Somalia were collected. DRTBOX is not mentioned, maybe because Dutch troops had left Afghanistan already by August 2010)
These numbers are very small compared to what NSA and American military units collected. They also, once again, show that "mass surveillance" of entire populations would require the collection of billions of metadata records rather than the millions that showed up in these particular charts (60 million would roughly be the number of metadata generated by 20.000 handsets).
In the second half of 2013, these charts were published in various major European newspapers saying that they proved that NSA monitored millions of phone calls in those countries. Soon it turned out this interpretation was completely wrong, something which co-author Glenn Greenwald only admitted in The Intercept's article from last May.
> See also: Dutch government tried to hide the truth about metadata collection
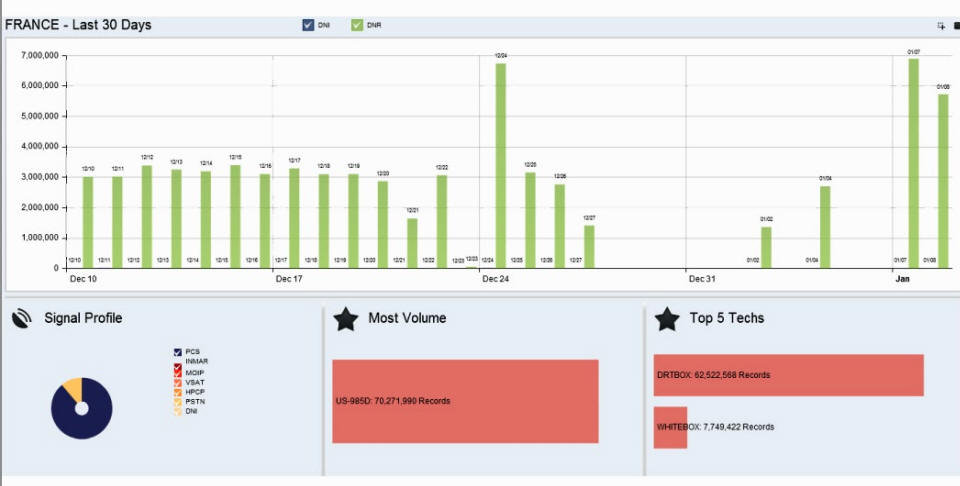
BOUNDLESSINFORMANT chart showing metadata collected by French intelligence, including 62 million records through the DRTBOX system
3rd Party partners
Interesting is that Polish troops in Afghanistan also got one DRT interception device and there's also a BOUNDLESSINFORMANT chart showing that in one month time they collected some 71 million cellphone metadata. But despite this effort, Poland did not become a member of the Afghanistan SIGINT Coalition.
Poland was also not a member of the SIGINT Seniors Europe, so it seems the AFSC was only meant for countries that were already part of the SSEUR. The slide at the top of this blog post shows that, together with several other NATO countries, Poland is listed in red as a "National SIGINT Partner".
Except for Slovenia, these National SIGINT Partners appear to be identical with the so-called 3rd Party partners, which are the (signals) intelligence agencies of over 30 countries with which NSA has a formal relationship. They are one level below the 2nd Party partners, or Five Eyes, who have a fully integrated signals intelligence cooperation.
> See also: NSA's Foreign Partnerships
Quid pro quo
The operations in Afghanistan show how many different levels of cooperation there can be: there were 3rd Party partners who did nothing more or less than ordinary NATO members. Among them, information is only shared up to the classification level SECRET.
Then there was Poland which collected and shared telephone metadata, but did not participate in the CENTER ICE platform through which the countries of the SIGINT Seniors Europe communicated and exchanged threat information at the level TOP SECRET/SI.
The closest cooperation for 3rd Party partners was in the AFSC, where they fed telephone metadata directly into the NSA's RT-RG system. Because cooperation between intelligence agencies is always based upon the principle of quid pro quo, these partners also got things in return, equal to their input.
For the members of the AFSC these returns included real-time data access, unique linguistic resources and joint counter insurgency operations - things that could have been crucial for the success of their operations or the safety of their troops, but which the Five Eyes did not make available to the (initially broader group of the) SIGINT Seniors Europe.
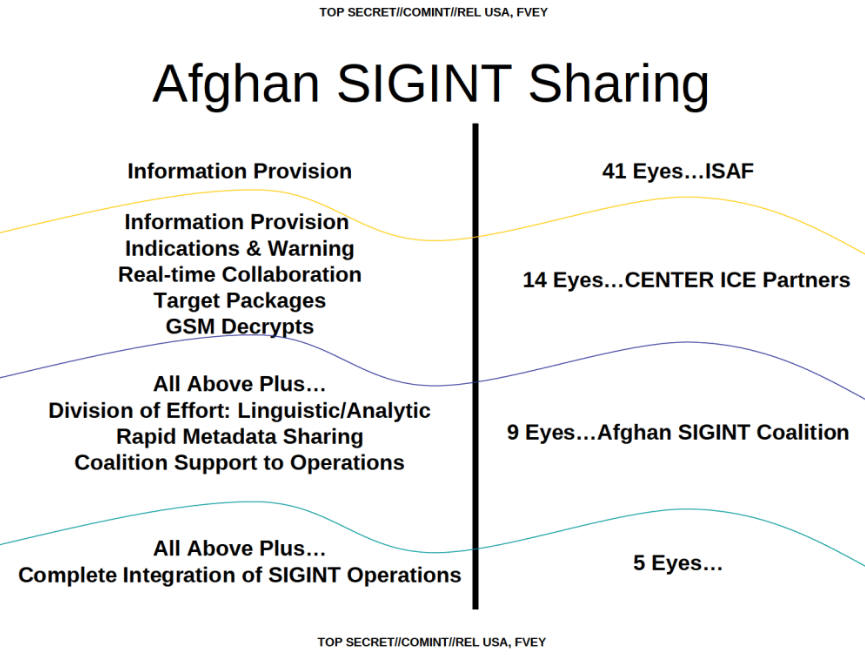
Epilogue
The latest document in which the Afghanistan SIGINT Coalition was mentioned is an NSA paper from April 2013. One month later there was an AFSC conference in Denmark at which would be discussed what to do after the ISAF mission would be disbanded in December 2014. It's not known whether there was any kind of continuation.
The Real-Time Regional Gateway proved to be so successful that already in 2012, NSA deployed the system at 11 locations around the world, including at its regional center in Texas to combat Mexican drug trafficking, as well as on board of the nuclear submarine USS Georgia, which collected mobile phone metadata around the Horn of Africa.
![]()
![]()
![]() New NSA/MOSSAD Cyber Operations Infrastructure Exposed
New NSA/MOSSAD Cyber Operations Infrastructure Exposed
May 02, 2019 - SIPERNET, PRISM and dozens of other programs were long ago exposed and made public so with the recent public announcements that the NSA was giving up a program they had allowed to be outed in a Limited Hangout Operation whose public face was the infamous CIA Avatar Edward Greenberg (Snowden) Black Hats and others who continue to operate in the Shadows began investigating as the CIA, the NSA or any other Intelligence Agency never gives up a program unless there is something better to replace it. The incestuous relationship that exists between the US Intelligence Community and the Corporations they use as Fronts, while being an evil key ingredient of Fascism and the creation of a Full SPectrum Dominance Total Surveillance Fascist Police State, one which they are trying to bring about worldwide, is a Godsend for Counter Intelligence Operations and those who wish to expose the evil that the US "Intelligence" Community is trying to spread worldwide in their drive for global domination.
Lies within lies, within enigmas, inside puzzles and obfuscated and covered up with disinformation, misinformations and carefully calculated obfuscation are almost useless when one knows what to look for and nine times out of ten the devil is in the money. Earlier we exposed and reported on Amazon's marriage to the CIA and thus their buy in into the Washington Post and as with that revelation this one is very similiar in that private individuals and corporations are being used to attempt to covertly install infrastructire worldwide. Unlike the CIA, which leaks like a boat made of Swiss cheese, the NSA is much more devious and this time not only have we caught the NSA but also MOSSAD as the connections to the owners of the bodies in question shows.
Exposing the evildoers is getting more and more dangerous and in some countries actually impossible with the almost complete taekover and control of the Internet by Western Intelligence Agencies but leaks and exposure are still possible as the following information is a testament to.
We would like to express our gratitude to our sources who have taken huge risks in getting this information and related documentation to us and pray that they are safe and that their risks are properly appreciated and valued by all of our dear readers.
![]()
![]() Meet AS53667 ~ PONYNET, Level(3) LLC, CenturyLink uCommand (Kosher), MOSSAD
Security Analyst Lawrence (Larry) Goldstein, Wayback Machine (Where ASIS and
WikiLeaks stored the Podesta files), American Locker Group Inc., Star Struck
Inc., Horizon Kinetics LLC and many more
Meet AS53667 ~ PONYNET, Level(3) LLC, CenturyLink uCommand (Kosher), MOSSAD
Security Analyst Lawrence (Larry) Goldstein, Wayback Machine (Where ASIS and
WikiLeaks stored the Podesta files), American Locker Group Inc., Star Struck
Inc., Horizon Kinetics LLC and many more
MOSSAD uses the Kosher sign in an at symbol for those in the know. Unfortunately for them this was not a very clever thing to do, but thanks! Their logo literally means Kosher Command.
https://www.bgpview.io/asn/53667#graph
Level 3 Parent, LLC
AS3549 ~ LVLT-3549
https://bgpview.io/asn/3549#info
https://bgpview.io/asn/3549#peers-v4
ASNumber: 3549
ASName: LVLT-3549
ASHandle: AS3549
RegDate: 2000-03-21
Updated: 2018-02-20
Ref: https://rdap.arin.net/registry/autnum/3549
OrgName: Level 3 Parent, LLC
OrgId: LPL-141
Address: 100 CenturyLink Drive
City: Monroe
StateProv: LA
PostalCode: 71203
Country: US
RegDate: 2018-02-06
Updated: 2018-02-22
Ref: https://rdap.arin.net/registry/entity/LPL-141
OrgTechHandle: IPADD5-ARIN
OrgTechName: ipaddressing
OrgTechPhone: +1-877-453-8353
OrgTechEmail: ipaddressing@level3.com
OrgTechRef: https://rdap.arin.net/registry/entity/IPADD5-ARIN
OrgAbuseHandle: IPADD5-ARIN
OrgAbuseName: ipaddressing
OrgAbusePhone: +1-877-453-8353
OrgAbuseEmail: ipaddressing@level3.com
OrgAbuseRef:
https://rdap.arin.net/registry/entity/IPADD5-ARIN
Operations
Level 3 Communications operates a large network Internet. This includes 46 states in the continental United States,[20][21] South America, Western Europe,[4][22] and some cities in Asia. It uses transatlantic cables,[23] including "Yellow" /AC-2 (on which it owned two of the four fiber pairs after Viatel's 2001 bankruptcy).[24]
Level 3 Communications has also purchased 300 Gbit/s of capacity on the Apollo (cable system).[25]
It is the current owner of AS1[26] (following the acquisition of Genuity, from BBN Technologies), but it uses AS3356 for operations. AS3356 as of 2007 consistently had one of the highest ranked connectivity degrees on the Internet.[27][28] It also operates the former Global Crossing network (AS3549) following the company acquisition in 2011.
Level 3 Communications delivers Netflix and Apple music and video content over the Internet.[29]
The company runs a content delivery network which it acquired from Savvis in
2006.[30]
In 2006, Level 3 Communications announced with Internet2, an academic
network, that they would deploy a next generation nationwide research
network.[31]
Sales organization
Level 3 distributes and sells its services through a mix of six independent sales channels: large enterprise, wholesale, federal, content and media, midmarket, and indirect. All six sales channels report to the president of sales Andrew Crouch.[32] The top performing Level 3 indirect sales agencies in 2010 include Intelisys, Microcorp, CDW/AVANT Communications, PlanetOne, Advantage Communications Group, Telarus, and Presidio.[33]
https://www.bgpview.io/asn/53667#graph
https://bgpview.io/asn/3549#peers-v4
Level 3 Communications, Inc.
http://www.level3.com
Aliases
IRS EIN 47-0210602, Kiewit Diversified Group Inc, Level 3 Communications
Parent
Phlcorp Holding LLC
Aliases Baldwin United Corp., Phlcorp, Inc.
https://web.archive.org/web/20190501132748/https://littlesis.org/org/116886-Phlcorp_Holding_LLC
Parent
Leucadia National Corporation
Aliases IRS EIN 13 -2615557, Leucadia National Corp
Owner
Horizon Kinetics LLC
http://www.hamincny.com/
https://web.archive.org/web/20170910193516/http://www.littlesis.org/org/87084-Horizon_Kinetics_LLC
Trump linked via Icahn Enterprises L.P. A diversified holding company
https://web.archive.org/web/20190501184109/https://horizonkinetics.com/research-reports/
Owner
FRMO Corporation
https://web.archive.org/web/20190501133945/https://littlesis.org/org/139374-FRMO_Corporation
https://web.archive.org/web/20190501183628/https://frmocorp.com/
Owned by
Lawrence J Goldstein
https://web.archive.org/web/20190501134847/https://littlesis.org/person/139382-Lawrence_J_Goldstein
https://web.archive.org/web/20190501135627/https://littlesis.org/person/148492/Lawrence_Goldstein
https://web.archive.org/web/20190501134847/https://littlesis.org/person/139382-Lawrence_J_Goldstein
Donation/Grant Recipients
AIPAC
https://web.archive.org/web/20190501141451/https://littlesis.org/relationships/759774
above list deleted from archive (Wayback machine is owned by level 3)
Other Affiliations*
American Locker Group Inc.
SMP Asset Management, LLC
Santa Monica Partners, L.P.
Fromex Equity Corp.
Vice President, Treasurer, Director and Vice President - Star Struck Inc.
Star Struck, Ltd.
Dual Israeli/US Citizen and MOSSAD Asset/Officer Lawrence Goldstein
Mr. Lawrence J. Goldstein, also known as Larry, is the Founding General Partner at Santa Monica Partners, L.P. He founded the firm in 1982.
Mr. Goldstein is the President at Santa Monica Partners Asset Management LLC, since January 2003.
He has been a Vice President, Treasurer, and Director of Star Struck Ltd., since 1985 and serves as a Vice President at Star Struck Inc.
Previously, Mr. Goldstein also managed the University of Michigan Business School Growth Fund for the twelve years of its existence.
Prior to founding Santa Monica Partners, he was the First Vice President at Drexel Burnham Lambert and a General Partner (Security Analyst and Fund Manager) of its predecessor Burnham & Company for 23 years. Mr. Goldstein is a Member of Advisory Board of Tudog Consulting, Inc.
He served as a Director of FRMO Corp until March 11, 2005.
Mr. Goldstein was also a Director of American Locker Group Inc., from February 2003 to March 19, 2004.
Google cache of Donation and Grant Recipients. The archived cache was also
archived.
it maybe usefull
The announcement below is like a literal "Who's Who" of Corporate Deep State Intelligence Connected Bodies
CenturyLink to acquire Level 3 Communications
The combined company will have the ability to offer CenturyLink's larger enterprise customer base the benefits of Level 3's global footprint with a combined presence in more than 60 countries. In addition, the combined company will be positioned to further invest in the reach and speeds of its broadband infrastructure for small businesses and consumers.
Highly Complementary Businesses with Expanded Fiber Networks: This transaction increases CenturyLink's network by 200,000 route miles of fiber, which includes 64,000 route miles in 350 metropolitan areas and 33,000 subsea route miles connecting multiple continents. Accounting for those served by both companies, CenturyLink's on-net buildings are expected to increase by nearly 75 percent to approximately 75,000, including 10,000 buildings in EMEA and Latin America.
Overall, the BofA Merrill Lynch and Morgan Stanley & Co. LLC acted as CenturyLink's financial advisors, and Evercore provided a fairness opinion. Wachtell, Lipton, Rosen & Katz and Jones Walker are acting as CenturyLink's legal advisors. Citigroup acted as financial advisor to Level 3, and Lazard provided a fairness opinion. Willkie Farr & Gallagher LLP acted as legal advisor to Level 3. Latham & Watkins acted as legal advisor and Credit Suisse acted as financial advisor to ST Telemedia.
https://web.archive.org/web/20190429012046/https://www.centurylink.com/
www.level3.com Redirect to the location below
https://web.archive.org/web/20190428173140/https://www.centurylink.com/business.html?rid=lvltmigration
https://web.archive.org/save/https://www.credit-suisse.com/fr/fr.html
A reference to PHAROAH
Supporting links of interest to investigators
https://portout.level3.com/Login.aspx?ReturnUrl=%2fCsrSubmit.aspx
https://account.level3.com/login
https://gsaportal.level3.com/login.jsp
https://vfoprod-level3.activationnow.com/
https://webmail.level3-hosting.com/
https://voiceconfig.level3.com/auth/login/
https://mediaportal.level3.com/ui/auth
https://ham.level3.com/Uberservices/WorkOrder/Index
https://portout.level3.com/CreateNewUser.aspx
https://myportal.level3.com/Login.aspx?ReturnUrl=%2fMyChangeRequests%2fMyChangeRequests.aspx
https://eisgsaportal.level3.com/
https://tokenreg.level3.com/selfEnrollment/Enrollment.aspx?tokenLoaded=true
http://your.level3.com/TheStateofTexas
https://gsaportal.level3.com/forgotPassword.jsp
https://www.2-spyware.com/remove-searchguide-level3-com-virus.html
http://irthnet.level3.com/IRTHNet/Logon.aspx
https://www.2-spyware.com/remove-searchguide-level3-com-virus.html
http://irthnet.level3.com/IRTHNet/Logon.aspx
![]()
![]() Shadow Brokers EQGRP Lost in Translation Resources
Shadow Brokers EQGRP Lost in Translation Resources
https://gist.github.com/iam1980/0155d277b03ec535291a1b0a788b3812
https://labs.nettitude.com/blog/a-quick-analysis-of-the-latest-shadow-brokers-dump/
![]()
![]()
![]() Snow Den Op
PRISM Leak Orchestrated by USMC/CIA Clinton, Obama and Neo Cons
Snow Den Op
PRISM Leak Orchestrated by USMC/CIA Clinton, Obama and Neo Cons
http://www.jar2.com/Topics/Snowden.html

![]()
![]()
NSA/Google Operation Enduring Security Framework
![]()
![]()
![]() NSA/CARNIVORE/PRISM/Et Al: Library Computer Keyword Lists
NSA/CARNIVORE/PRISM/Et Al: Library Computer Keyword Lists
http://www.jar2.com/2/NSA/NSA_KEYWORDS.html
![]()
![]()
![]() NSA Black Budget: TOP SECRET
NSA Black Budget: TOP SECRET
Budget reveals black operations, programs and much more about the US' most secret agency
![]()
![]()
![]() NSA Post Hypnotic Subliminal Scripts - MKULTRA/MOCKINGBIRD on Steroids
NSA Post Hypnotic Subliminal Scripts - MKULTRA/MOCKINGBIRD on Steroids
![]()
![]()
![]() The NSA Tools:
THIS HUGE RELEASE IS
DEDICATED TO VITALY CHURKIN AND ALL THE GOOD PEOPLE KILLED BY THE
NSA/CIA/MOSSAD AND THEIR AGENTS
The NSA Tools:
THIS HUGE RELEASE IS
DEDICATED TO VITALY CHURKIN AND ALL THE GOOD PEOPLE KILLED BY THE
NSA/CIA/MOSSAD AND THEIR AGENTS
http://www.jar2.biz/Files/NSA_TOOLS/EQGRP-master.zip

![]()
![]()
![]() UNENCRYPTED ZIPPED FILE: DOWNLOAD AT YOUR OWN RISK
UNENCRYPTED ZIPPED FILE: DOWNLOAD AT YOUR OWN RISK
http://www.jar2.biz/Files/NSA_TOOLS/EQGRP-master.zip
![]()
![]()
![]() SOURCE of FILES: The Shadow Brokers, Analysis by GITHUB, HOSTING by JAR2 BIZ
SOURCE of FILES: The Shadow Brokers, Analysis by GITHUB, HOSTING by JAR2 BIZ
MESSAGE FROM SHADOW BROKERS:
https://github.com/x0rz/EQGRP/blob/master/README.md
Unknown
COTTONAXE
EBBISLAND related rce
STOICSURGEON
INCISION
ITIME
JACKLADDER
DAMPCROWD
ELDESTMYdLE
SUAVEEYEFUL
WATCHER
YELLOWSPIRIT
![]()
Misc
DITTLELIGHT (HIDELIGHT) unhide NOPEN window to run unix oracle db scripts
DUL shellcode packer
egg_timer execution delayer (equivalent to at)
ewok snmpwalk-like?
gr Web crontab manager? wtf. NSA are webscale dude
jackladderhelper simple port binder
magicjack DES implementation in Perl
PORKSERVER inetd-based server for the PORK implant
ri equivalent to rpcinfo
uX_local Micro X server, likely for remote management
![]()
Remote Code Execution
Solaris
CATFLAP Solaris 7/8/9 (SPARC and Intel) RCE (for a LOT of versions)
EASYSTREET/CMSEX and cmsd Solaris rpc.cmsd remote root
EBBISLAND/ELVISCICADA/snmpXdmid and frown: CVE-2001-0236, Solaris 2.6-2.9 -
snmpXdmid Buffer Overflow
sneer: mibissa (Sun snmpd) RCE, with DWARF symbols :D
dtspcdx_sparc dtspcd RCE for SunOS 5. -5.8. what a useless exploit
TOOLTALK DEC, IRIX, or Sol2.6 or earlier Tooltalk buffer overflow RCE
VIOLENTSPIRIT RCE for ttsession daemon in CDE on Solaris 2.6-2.9 on SPARC
and x86
Netscape Server
xp_ns-httpd NetScape Server RCE
nsent RCE for NetScape Enterprise server 4.1 for Solaris
eggbasket another NetScape Enterprise RCE, this time version 3.5, likely
SPARC only
FTP servers
EE proftpd 1.2.8 RCE, for RHEL 7.3+/Linux, CVE-2011-4130? another reason not
to use proftpd
wuftpd likely CVE-2001-0550
Web
ESMARKCONANT exploits phpBB vulnerability (<2.0.11)
ELIDESKEW Public known vulnerablity in SquirrelMail versions 1.4.0 - 1.4.7
ELITEHAMMER Runs against RedFlag Webmail 4, yields user nobody
ENVISIONCOLLISION RCE for phpBB (derivative)
EPICHERO RCE for Avaya Media Server
Misc
calserver spooler RPC based RCE
EARLYSHOVEL RCE RHL7 using sendmail
ECHOWRECKER/sambal: samba 2.2 and 3.0.2a - 3.0.12-5 RCE (with DWARF
symbols), for FreeBSD, OpenBSD 3.1, OpenBSD 3.2 (with a non-executable
stack, zomg), and Linux. Likely CVE-2003-0201. There is also a Solaris
version
ELECTRICSLIDE RCE (heap-overflow) in Squid, with a chinese-looking vector
EMBERSNOUT a remote exploit against Red Hat 9.0's httpd-2.0.40-21
ENGAGENAUGHTY/apache-ssl-linux Apache2 mod-ssl RCE (2008), SSLv2
ENTERSEED Postfix RCE, for 2.0.8-2.1.5
ERRGENTLE/xp-exim-3-remote-linux Exim remote root, likely CVE-2001-0690,
Exim 3.22-3.35
EXPOSITTRAG exploit pcnfsd version 2.x
extinctspinash: Chili!Soft ASP stuff RCE? and Cobalt RaQ too?
KWIKEMART (km binary) RCE for SSH1 padding crc32 thingy
(https://packetstormsecurity.com/files/24347/ssh1.crc32.txt.html)
prout (ab)use of pcnfs RPC program (version 2 only) (1999)
slugger: various printers RCE, looks like CVE-1999-0078looks
statdx Redhat Linux 6.0/6.1/6.2 rpc.statd remote root exploit (IA32)
telex Telnetd RCE for RHEL ? CVE-1999-0192?
toffeehammer RCE for cgiecho part of cgimail, exploits fprintf
VS-VIOLET Solaris 2.6 - 2.9, something related to XDMCP
SKIMCOUNTRY Steal mobile phone log data
SLYHERETIC_CHECKS Check if a target is ready for SLYHERETIC (not included)
EMPTYBOWL RCE for MailCenter Gateway (mcgate) - an application that comes
with Asia Info Message Center mailserver; buffer overflow allows a string
passed to popen() call to be controlled by an attacker; arbitraty cmd
execute known to work only for AIMC Version 2.9.5.1
![]()
Anti-forensic
toast: wtmps editor/manipulator/querier
pcleans: pacctl manipulator/cleaner
DIZZYTACHOMETER: Alters RPM database when system file is changed so that RPM
(>4.1) verify doesn't complain
DUBMOAT Manipulate utmp
scrubhands post-op cleanup tool?
Auditcleaner cleans up audit.log
![]()
Control
Iting HP-UX, Linux, SunOS
FUNNELOUT: database-based web-backdoor for vbulletin
hi UNIX bind shell
jackpop bind shell for SPARC
NOPEN Backdoor? A RAT or post-exploitation shell consisting of a client and
a server that encrypts data using RC6 source
ORLEANSTRIDE
SAMPLEMAN / ROUTER TOUCH Clearly hits Cisco via some sort of redirection via
a tool on port 2323... (thanks to @cynicalsecurity)
SECONDDATE Implant for Linux/FreeBSD/Solaris/JunOS
SHENTYSDELIGHT Linux keylogger
SIDETRACK implant used for PITCHIMPAIR
SIFT Implant for Solaris/Linux/FreeBSD
SLYHERETIC SLYHERETIC is a light-weight implant for AIX 5.1-5.2 Uses
Hide-in-Plain-Sight techniques to provide stealth.
STRIFEWORLD: Network-monitoring for UNIX, needs to be launched as root.
Strifeworld is a program that captures data transmitted as part of TCP
connections and stores the data in a memory for analysis. Strifeworld
reconstructs the actual data streams and stores each session in a file for
later analysis.
SUCTIONCHAR: 32 or 64 bit OS, solaris sparc 8,9, Kernel level implant -
transparent, sustained, or realtime interception of processes input/output
vnode traffic, able to intercept ssh, telnet, rlogin, rsh, password, login,
csh, su, …
CnC
Seconddate_CnC: CnC for SECONDDATE
ELECTRICSIDE likely a big-fat-ass CnC
NOCLIENT Seems to be the CnC for NOPEN*
DEWDROP
![]()
Privesc
Linux
h: linux kernel privesc, old-day compiled hatorihanzo.c, do-brk() in 2.4.22
CVE-2003-0961
gsh: setreuid(0,0);execl("bash","/bin/bash")
PTRACE/FORKPTY/km3: linux kernel lpe, kmod+ptrace, CVE-2003-0127,
(https://mjt.nysv.org/scratch/ptrace_exploit/km3.c)
EXACTCHANGE: NULL-deref based local-root, based on various sockets
protocols, compiled in 2004, made public in 2005
ghost:statmon/tooltalk privesc?
elgingamble:
ESTOPFORBADE local root gds_inet_server for, Cobalt Linux release 6.0, to be
used with complexpuzzle
ENVOYTOMATO LPE through bluetooth stack(?)
ESTOPMOONLIT Linux LPE
EPOXYRESIN Linux LPE
AIX
EXCEEDSALON-AIX privesc
![]()
Others
procsuid: setuid perl (yes, it's a real thing) privesc through unsanitized
environnement variables. wtf dude
elatedmonkey: cpanel privesc (0day) using
/usr/local/cpanel/3rdparty/mailman/. Creates mailman mailing list: mailman
config_list
estesfox: logwatch privesc, old-day
evolvingstrategy: privesc, likely for Kaspersky Anti-virus
(/sbin/keepup2date is kaspersky's stuff) (what is ey_vrupdate?)
eh OpenWebMail privesc
escrowupgrade cachefsd for solaris 2.6 2.7 sparc
ENGLANDBOGY local exploit against Xorg X11R7 1.0.1, X11R7 1.0, X11R6 6.9,
Includes the following distributions: MandrakeSoft Linux 10.2, Ubuntu 5.0.4,
SuSE Linux 10.0, RedHat Fedora Core5, MandrakeSoft Linux 2006.0. requires a
setuid Xorg
endlessdonut: Apache fastcgi privesc
![]()
Interesting stuff
default passwords list (courtesy of x0rz)
gov.ru (stoicsurgeon_ctrl__v__1.5.13.5_x86-freebsd-5.3-sassyninja-mail.aprf.gov.ru) (wow
![]()
![]()
![]() 2013 Re-Release: Why Was This Ignored by the Russian Media?
2013 Re-Release: Why Was This Ignored by the Russian Media?
NSA_Catalog.zip
NSA_Quantum_Tasking.pdf
NSA_Quantum_Theory.pdf
2013 NSA_Catalog_Greenberg_Appelbaum_Burn.pdf

![]()
![]()
![]()
![]() PRISM
PRISM
http://www.jar2.com/Topics/PRISM.html

![]()
![]()
![]() Mass Protests Planned Against NSA Mass
Surveillence
Mass Protests Planned Against NSA Mass
Surveillence
10 February, 2014 15:04
Worldwide protests against NSA led mass
surveillance are planned for November 11, 2014 in a protest billed by
organizers as “The Day We Fight Back”. Although the protest actions are
largely US based and even the countdown clock is timed to US Pacific Time,
the on-line activities and protests will affect internet users worldwide as
many of the world’s top sites are joining in.
The planned activities on the cyber front are being
led by the Internet Defense League, a group of which led the Internet
blackout that effectively killed the US Stop Online Piracy Act (SOPA) and
Protect IP Act, attempts by the US Government to bring the Internet under
complete censorship and control. Those protests were successful in
permanently shelving SOPA and PIPA and now the hope of the organizers is
that tomorrow’s actions will reign in the NSA, and by default its spying
network FVEY, and shelve a new bill sponsored by US Senator Dianne Feinstein
called the FISA Improvements Act, as well as garner support for what is
called the USA Freedom Act and finally enact protections for non-Americans.
In a statement released by the Internet Defense
League website the organizers say the new protests are planned in memory of
Mr. Aaron Swartz, the creator of RSS technology, one of the founders of
Reddit and an Internet activist who was persecuted for sharing taxpayer
funded research material from the Massachusetts Institute of Technology
(MIT) JSTOR (Journal Storage) system.
Although the research material and academic
journals downloaded by Mr. Swartz were not secret in nature and publically
funded, over-zealous prosecutors sought to force Mr. Swartz to pay a $1
million fine and serve 35 years in prison. Mr. Swartz, his lawyers and
supporters fought the US Government’s case to no avail and after his second
plea bargain offer was denied by prosecutors who sought to make him pay the
maximum penalty, Mr. Swartz was found dead in his New York apartment having
been persecuted into apparently committing suicide.
Aaron Swartz was instrumental in organizing the
anti-SOPA/PIPA protests, which many believe was the real reason the US
Government persecuted him on the trumped up charges for downloading academic
journals. The US was desperate to prosecute high-profile Hacktivists and in
the end, as with many of their heavy handed persecutions, they turned him
into a legend and a martyr for the cause of internet freedom and the right
of the people to benefit from academic work that they in fact pay for but
are not allowed to openly see or use.
The participants of the Day We Fight Back protests
so far include such respected organizations as the Electronic Frontier
Foundation, the ACLU, the Freedom of the Press Foundation, Reddit, Mozilla
and Amnesty International but it is yet to be seen if giants like Google and
Wikipedia will be taking part, as of publication it is still not clear.
Two years ago the internet blackout against
SOPA/PIPA included the participation of Wikipedia and Google, whose support
was instrumental in bringing an end to proposed SOPA/PIPA legislation. That
protest, according to SOPA Strike dot com also included the blacking out of
sites such as Reddit, Wordpress, Tumblr, Drudge Report, Wired and over
115,000 other sites. The unprecedented resistance to SOPA/PIPA also gathered
10 million signatures on a petition, over 8 million phone calls to
legislators, more than 4 million e-mails sent and caused over 1 billion
users to be blocked from websites.
The organizers of the February 11th protests say
there will not be an internet blackout but that banners will be spread all
over the internet and on prominent sites calling for people in the US to
call or e-mail the US Congress in protest of the FISA Improvements Act and
in support of the USA Freedom Act. Internationally the organizers are asking
for supporters of internet freedom to urge their proper authorities to
institute privacy protections for Internet users.
In the statement
released on the day we fight back dot org, organizers say:
“Together we will push
back against powers that seek to observe, collect, and analyze our every
digital action. Together, we will make it clear that such behavior is not
compatible with democratic governance. Together, if we persist, we will win
this fight.”
So far there are no calls for international
targeting of NSA partners by the organizers and there is no mention of
protesting the intelligence organizations which make up the FVEY signals
intelligence alliance which are vital for the NSA’s global reach.
Realistically for the world’s Internet users protests should also include
NSA partners and the signals intelligence organizations of the NSA’s FVEY
alliance as well. These include Australia’s Australian Signals Directorate
(ASD), Canada’s Communications Security Establishment Canada (CSEC), New
Zealand’s Government Communications Security Bureau (GCSB) and the United
Kingdom’s Government Communications Headquarters (GCHQ).
On a global level protesting the NSA and instituting or opposing US legislation means little or nothing when the NSA’s foreign subordinates are pulling most of the weight for the NSA on the international arena. However this may also point to the NSA’s subordination of its FVEY partners. Tellingly such intrusive surveillance as is being carried by FVEY on its own citizens is not being protested in other countries such as Russia, where the internet remains largely as free as it was at the time of its inception.
![]()
![]()
![]() NSA: no terrorists caught, yet entangled in everything - By John Robles
NSA: no terrorists caught, yet entangled in everything - By John Robles
31 January , 2014 12:29
There is so much missing or purposefully obfuscated in the debate about
NSA/Five Eyes spying, US Government illegality, CIA collusion with al-Qaeda,
Guantanamo, 9/11, torture, drones, Afghanistan, Iraq and everything that
millions of people have been outraged about for over a decade, but the most
striking is that almost no one is proposing closing these organizations down
and few are talking about prosecuting those responsible.
The glaring problem that everyone seems to be missing or purposefully
avoiding, the elephant in the room if you will, is that everything that has
been revealed by Edward Snowden and debated about endlessly is completely
illegal and for a government and a "secret agency" indefensible, but due
America's self promoted "exceptionalism" everyone finds it more comfortable
to avoid such talk. In reality the NSA must be shut down but everyone in the
West and in the western controlled corporate media do not dare to even
debate this issue.
The NSA, as a secret organization whose initials stood for "No Such Agency"
20 years ago, has failed to maintain its secrecy and has gone from being the
most secret agency of the US Government to a common household word. This is
unacceptable in the world of espionage and the fact that a large quantity of
its dirty laundry is available on-line and debated on a daily basis should
be reason enough for the whole agency to be shut down. From a security
standpoint in allowing leak after leak culminating in the mania that has
become Edward Snowden the agency has proven that it is porous, prone to
leakage and unable to maintain its secrets. These words are words that
should be said by someone on the US Senate Intelligence Committee in serious
hearings not by a Russian journalist but we have seen that US politicians,
the US President and the US mass-media are completely impotent when it comes
to oversight or dealing with real threats to security and even worse than
impotent but complicit when it comes to illegality committed by any
government body or their security structures.
NSA/CIA etc Illegality, Ineffectiveness
In an article for Global Research by James Corbett dealing with the
choreographed media operations that the NSA is engaged in continuing its
illegality and escaping oversight. In the article Mr. Corbett writes that
prior to 9-11 the NSA was already spying on all Americans, was tracking Bin
Laden and Al-Qaeda (the CIA's Data-Base) and then withholding that
information from the CIA's Bin Laden unit. In other words the NSA could have
prevented 9-11 if it was in fact carried out by Al-Qaeda but did not and
then used the event, according to Mr. Corbett to say it needed more powers
and to justify its illegal surveillance of Americans.
This usage of 9-11 as a blanket reason to justify all form of US Government
CIA/NSA etc. illegality has grown truly tired and unbelievable. From the
crimes against humanity that were the invasions of Afghanistan and Iraq, to
the illegal torture prison at Guantanamo, to the illegal extra-judicial
execution by drone program and finally to the blanket surveillance of all
Americans 9-11 has been the justification. 9-11: events which have not even
been properly explained or investigated and will never be because they were
the basis for all of the other illegality.
Recently ex MI5 officer David Shayler put it this way in a VoR interview: "…
if we stop funding government, it stops funding this nonsense, it stops
funding things like the NSA and MI5 and MI6. And it is not like we are going
to be attacked if these organizations disappear, because as I say they are
causing most of the conflict on the planet in the first place."
Mr. Shayler is not alone in having the bravery to say what has to be said
and the public record bears his words out that these agencies are truly the
root of all evil and are not engaged in defense or protection but rather in
hiding illegality and assuring their own continued funding and illegal
conduct and operations.
In an article for wired dot com
David Kravets recently wrote
about
how the NSA's spying was illegal, ineffective and should be stopped: "Based
on information provided to the Board, we have not identified a single
instance involving a threat to the United States in which the telephone
records program made a concrete difference in the outcome of a
counterterrorism investigation," the report found. "Moreover, we are aware
of no instance in which the program directly contributed to the discovery of
a previously unknown terrorist plot or the disruption of a terrorist
attack."
Even though one judge did find it illegal, the NSA just found another judge
who it owned to say it wasn't. As for not preventing a single terrorist
attack, well let the record speak for itself. If the NSA with its billion
dollar budget and the supposed ability to monitor, intercept and store
everything anyone says or does through any sort of electronic communication
and has been doing so since before 9-11 then why are they unable to show
even 1 single terrorist attack that they have prevented? And why were they
not able to prevent 9-11 itself, since they could have as the record shows.
Could it be that 9-11 was really an inside job?
I dare say if any such organization existed in Russia heads would roll and
the whole operation would be shut down. What are they really doing in the
billion dollar Puzzle Palace? Playing video games?
They answer to that is undoubtedly no. They are spying on the world and
every single citizen of this planet that they can collect data on to
guarantee the continuity of the illegal security state, the profits of the
paper bankers and the continued existence of the US military industrial
complex. Oh and according to Mr. Corbett collecting data on foreign leaders
with which to blackmail them with. That used to be the domain of the CIA and
the FBI but that is the subject of another discussion.
Oversight
If you are reading this think about this for a minute: why is this appearing
on Russian media being written about by a Russian journalist? Is it because
Russia is somehow involved or cares about the NSA? No Russia has enough of
its own headaches to deal with but last summer the entire illegal US
security paradigm was unwontedly dumped in Russia's lap in the form of
American Patriot Edward Snowden who was not a Russian agent, had no
connection to Russia nor had even ever been on the territory of the Russian
Federation. Even worse for Russia is that Snowden is an unapologetic and
outspoken American patriot and an agent of both the CIA and the NSA. Not the
normal type of person Russia should or does protect.
Think about this as well if the US mass media was performing its function
and if the US president and the government he is supposed to be leading were
doing their jobs and serving the interests of the American people by holding
those committing illegality accountable, most of the illegality that has
been debated in the world media about the US since 9-11 would not have even
come to light and all of the matters that I have written about over the
years would not have been necessary. But the US is not capable of conducting
proper oversight nor of hiding its own illegality, it is out there for the
world to see debate and apparently to accept.
That is the key problem in the US. There is no oversight and the last
instance of oversight, the president himself, is also a party to the
illegality. Terror Tuesdays and Guantanamo prove this. Although it is not
entirely his fault, he is afraid of being assassinated no doubt if he does
not follow the instructions of the military industrial complex as the
Kennedy assassination proved. It is the CIA and the military industrial
complex that has the real power in the US and the people are merely an
abstraction for them that must serve the state and not the other way around.
Useless US Fourth Estate
As Mr. Corbett writes the mass media in the US is completely useless in
performing the function of the Fourth Estate. This has been said hundreds of
times before, he is not the only one saying this, and the case of Julian
Assange and WikiLeaks bears this out. The US corporate mass media is bought
and paid for and is merely a propaganda tool for the US military industrial
complex, bankers and the US Government which they now own.
Medea Benjamin recently put it this way in a VoR interview: "… there is not
a lot of information through the mainstream channels that can educate the
American people and just to circle back to the issue of Guantanamo I would
think that if there would be a poll done that most Americans wouldn't even
know that we still have people in Guantanamo. They probably think everybody
there was let go, it has been shut down or if they thought that anybody was
left it is because they have been tried and convicted and happened to be the
worst of the worst which is not true at all. So, unfortunately I think that
a lot of the reasons that the Administration can get away with policies like
this is because the US mainstream media has not been doing its job."
Ex NSA analyst
Wayne Madsen recently told me
that even Ted Turner, the founder of CNN admitted that the entire mass media
is "messed up" in the US. Mr. Madsen stated: "Ted Turner told me himself, at
the United Nations a few years ago that if it had to do it all over again,
he wouldn't have gotten into that deal with Time Warner and AOL, that
destroyed the network but it is too late. So, CNN can attack me all day
long. Its founder told me that 'they are screwed up', so I will take his
word over Wolf Blitzer or any of those clowns at CNN, I will take Ted
Turner's word over anything they have to say."This was predicted by John F
Kennedy in one of his most famous speeches to the US media. The military
industrial complex has taken over.
Recently Jessica Raddack, none other than a legal advisor for Edward
Snowden, recently told me in an interview
that Snowden did not take 1.7 million files as the world media are
reporting, yet not one single media outlet picked up on that fact because it
runs counter to the official US Government lie. Nor has any media taken
issue with the fact that all of the Snowden revelations are approved by the
US Government first. Ms. Raddack, perhaps unintentionally also let it be
known that all of the journalists who are publishing Snowden's "revelations"
are running them by the US Government first: "Well, in terms of 1.7 million
number, I've seen that a couple of times and it is coming from the
government. And as far as I know Mr. Snowden, according to the journalists
who received the documents, the number is really 55,000. I'm not sure if
that refers to 55,000 pages or files, but the number is far less than 1.7
million. And this is a first time I have heard that 1.7 million pertain to
military documents, ongoing military operations, JSOC (Joint Special
Operations Command) and things of that nature. I am not aware of the content
of the remaining files and I'm not worried about any damage resulting
because the documents were all given to respectable journalists here in the
US who have been carefully writing these articles and running them by the
government for approval before they are released."
So there you go. Even the NSA leaks are controlled.
Whistleblowers
The NSA and the US Government, rather than protecting their public from
terrorists and upholding the law and the rights of its citizens (I won't
even mention abiding by international law) are instead engaged in, as I have
already mentioned, operations to hide and obfuscate their own illegality.
This is something no doubt the American taxpayer would not agree to. This is
why they have waged a war on journalists and whistleblowers.
Regardless of Mr. Snowden's real "mission" as he keeps saying he has
"accomplished his mission" yet nothing much has changed, other than the
entire world now thinking the NSA is capable of spying on everyone and has
complete control of the internet (perhaps that was his mission?) he is seen
as a whistleblower and is apparently hunted by the US Government, just the
latest in a long list of enemies of the US. There has to be a point when the
world and the US public wake up and say enough is enough, and that is what
the NSA and FEMA and the rest of the US apparatus are truly afraid about.
How many years is poor Mr. Julian Assange going to live in an embassy room?
How many years is Edward Snowden not going to be allowed to return to his
beloved America? How many years is the illegal detention of the human beings
at Guantanamo going to continue? How long are they going to continue to hold
Bradley Manning, Jeremy Hammond and the rest? How long is the world going to
have to ignore the illegal Guantanamo torture prison and the illegal wars
and crimes against humanity? Forever? Unfortunately that is what they want
and once the complete control of the world media is obtained (including an
end to this journalist who has struggled to give a platform to
whistleblowers and truth seekers) and the entire planet is within range of
NATO nuclear warheads, that is what they will have. Complete impunity until
the end of time and a populace plugged into their devices ogling Britney
Spears and Lady Gaga.
Damage Control
The media is completely complicit and there is almost no way to fight them
then they control everything
Media operations Raddack
Note from the author:
As this article deals with the NSA and the US Government and the US
corporate controlled mass media with reference to globalists and big banking
and monied interests it is very unlikely that it will go viral or even
obtain a normal place in Google so I kindly ask: Dear reader if you are
reading this you probably look for alternative sources of information
because you know everything the mass media feeds you is tainted and much of
it is untrue, please share with anyone you think needs to hear the truth, no
matter how ugly it might be.
Thanks,
John
![]()
![]()
![]() Free net means no NSA, HRW finally speaks out
Free net means no NSA, HRW finally speaks out
January 21 2014
While Obama has pretended to address the issue of
mass surveillance, in a recent speech which some had expected would be
filled with promises to reign in the massive US spying apparatus, Obama said
absolutely nothing tangible and was blasted by privacy advocates,
whistleblowers and a plethora of interested parties, experts and pundits.
Now in a yearly 667 page report for 2013 released
in Berlin, Human Rights Watch (HRW) is warning that the revelations of
massive spying by the US will cause countries to install controls to keep
their users’ data within their own countries and that this will lead to
internet censorship in countries with poor human rights records (no mention
of US).
In the report HRW says that NSA spying revelations
may cause countries such as China or the Gulf States to:"… force user data
to stay within their own borders, setting up the potential for increased
internet censorship".
Of course I would say this is a no brainer, such
revelations should be forcing all governments to protect their citizens’
data from intrusive NSA spying but in doing so they will be getting in the
way of and interfering with the US, the NSA and their FVEY partners’ efforts
to mine the data of the entire planet.
Protecting the data of their citizens is every
country’s responsibility and must be done, therefore such an argument seems
disingenuous and it is also interesting to note that Human Rights Watch has
been all but silent to the plight of information activists and free internet
proponents until now.
To date HRW has had very little to say regarding
internet privacy and censorship inside the United States and has also been
all but silent as to the cases of Julian Assange, Bradley Manning and Jeremy
Hammond, but all of a sudden is concerned with data being unavailable or
“censored” and with internet freedom and free speech.
To their credit HRW did
chide the US Government for their callousness to privacy rights:
"The Snowden
revelations have made clear that there has been an intrusion on our right to
privacy of unprecedented scope, yet the government is dismissing any
complaints about our right to privacy as irrelevant."
The director of Human
Rights Watch Kenneth Roth (a former prosecutor) told the Guardian that:
“… one of the biggest missteps the US administration had committed was to
insist that there was a difference between the content of private
communication and "metadata" – information about where, when and between
whom the communication takes place.”
Mr. Roth put things
into perspective quite well stating:
"Imagine the government putting a video camera
in your bedroom and saying 'don't worry, the feed will only go into a
government computer, which we won't look at unless we have reason to believe
that wrongdoing is taking place.”
Finally regarding national data protection from a
technical standpoint it would be possible to block NSA to a large extent and
protect the user data of citizens and this has nothing to do with
censorship. Arguing that firewalling a country’s internet from NSA would
lead to censorship is completely absurd.
Monitoring takes place by governments regardless of
what the NSA is accessing and data protection and censorship are two
different animals, of course for the US and its partners in internet
tyranny, spying and control, anything countries do to keep them out will
have to be demonized.
![]()
![]()
![]() NSA/GCHQ/FVEY Spying on Everything: White
Sheds on Embassies are SIGINT Posts
NSA/GCHQ/FVEY Spying on Everything: White
Sheds on Embassies are SIGINT Posts

US embassy in Moscow.With 'spy box' on its roof.
By John Robles,
12 November,2013
12:55
While much
of the world’s attention has been focused on NSA and US spying through the
internet and electronic devices, one area that has been overlooked are
advances in/and activities surrounding signals intelligence through the
radio spectrum. An area which has also made huge advancements over the last
20 years.
One of the
key points for collecting foreign intelligence for almost any country are
the embassies and diplomatic missions of the word’s states abroad and with
the revelations by Edward Snowden of NSA servers based in US Embassies
worldwide, this has once again placed a focus on the sovereign territories
of countries as embodied by their diplomatic missions.
If one
drives by the US Embassy in Moscow and looks up one might notice a white
shed-sized "box" situated prominently almost directly in the middle of the
embassy’s roof. But what is it? Well the answer is most likely a camouflaged
spy post.
I
contacted a source with expertise in Signals Intelligence (SIGINT) about the
"boxes", which appear on US and UKUSA member embassies worldwide and he/she
said the white "sheds" are actually called "Secure Compartmented
Intelligence Facilities" (SCIF).
The source
said that there are two types of installation, some are temporary and
portable and some are permanent. The temporary or portable structures are
covered with a white material which is apparently a "modified
Kevlar made material that allows RF through with minimal attenuation."
The
permanent locations such as on the US Embassy in Moscow and the US Embassy
in Berlin have "dielectric
windows (a dielectric window is not made of glass but it is transparent to
radio waves ) which hide the specialist antennae and amplifiers, codenamed
EINSTEIN and CASTANET respectively".
The source
said that the specific frequency capability is dictated by the target
frequencies and the structures allow for multiple intercepts including:
data, voice, and whatever else they can receive.
The
innocent looking "boxes" are not only based all over the world on the roof
tops of embassies worldwide but they are all part of a global spy network
with the codename "STATEROOM". It is part of a "Special Collection Service"
or (SCS) apparently placed with the knowledge and participation of the
FiveEyes (FVEY) (UKUSA) participants or USUKCANAUSNZ.
As I have
written before UKUSA is a SIGINT alliance of the same "Five Eyes" countries,
United States, United Kingdom, Canada, Australia and New Zealand.
The source
says that there is no evidence of such SCIFs being mounted in FVEY countries
and that he/she suspects that this is due to hard connections available to
the four others who then share their take with the hosting nation; meaning
that no nation spies on its own, hence you have the UK’s GCHQ passing
information on UK citizens to the NSA, and Australia’s DSD, Canada’s CSEC
and New Zealand’s CSO doing the same, with the NSA apparently providing the
other four with the same level of data on their own citizens. The
relationships allow for the FVEY countries to spy on their own citizens by
having a "foreign" partner do it for them, thus skirting all of their own
national laws and constitutions.
The source
was asked about a cylindrical shaped structure on top of the UK Embassy in
Berlin and stated that he/she thought it was not part of STATEROOM .
The source
speculated that it could possibly be a probe into the beamwidth of a
telephone microwave link.
Although
the obvious targets of such surveillance are Chancellor Merkel and her
Government Offices (German High Command) the source says, the dielectric
window on the UK Embassy in Berlin is 90 degrees and one pane is pointing
over the top of the British Embassy towards the Russian Embassy on the
Brandenburg Gate a minutes’ walk away.
On the
11th September a man by the name of Ali Mansouri, an alleged member of the
Iranian Quds Force, was arrested for espionage operations in Israel.
In his
possession were photographs of various sites including the US Embassy in Tel
Aviv which actually showed the SCIF atop the building. The media release on
his arrest was not until the 29th of September so possibly, according to the
source: "… intelligence agencies such as the German BND were taking a look
atop the US Embassy in the Pariser Platz."
So that
takes care of the white "boxes" and other structures and designs on the
roofs of FVEY Embassies, now what about the NSA servers in the basements?
Kind of hard to photograph those I guess.
![]()
![]()
![]() NSA: Users lose in Skype/PRISM spying
NSA: Users lose in Skype/PRISM spying
By John Robles, 15 October, 22:10



Microsoft and its instant messaging and voice over IP provider Skype are
under investigation by the Luxembourg's data protection commissioner for
providing access to user data and communications to the United States
National Intelligence Agency (NSA).
Although Skype, a company that has had its share of legal actions in the
past, has been bought out by Microsoft Corporation, based in Redmond
Washington in the USA, it is being investigated for passing information to
the NSA by the European country because it has its headquarters in
Luxembourg.
It is not clear exactly when Skype began passing information and allowing
access to their data by US signals intelligence and spy agencies, and if it
was after or before the Microsoft takeover, but it is clearly a disturbing
development that a European based company has allowed itself to be used as a
spy tool on European and in fact on users around the word.
A report by the UK’s Guardian points to pre Microsoft takeover spying by
Skype, with a report saying that after the $8.5 billion acquisition by the
computer and IT behemoth, data flow to the NSA increased by 300%. The
Guardian also underlines the fact that Microsoft, one of the world’s richest
corporations, which in fact produces almost nothing tangible, was the first
to sign on to PRISM, a fact from which an number of conclusions can be
reached.
Not only is this an incursion into the privacy of all users affected, but it
is another serious incursion onto the sovereignty of yet another nation.
This is not something that should be allowed to be hushed up ignored and
allowed to be accepted as though it were something normal. It may seem like
a minor manner due to the sheer magnitude of the NSA and CIA spying
“apparati” and this is disturbing.
It is also disturbing that it appears that the fact that Skype is being
investigated for allowing itself to become part of the infamous massive
PRISM program is getting more attention from people around the world and the
media than the revelations by Edward Snowden that they were in fact spying
in the first place.
The world has grown so accustomed it would appear, to US infringement on
their rights, privacy and territory that it is bigger news when someone
challenges them or their proxies in any way, shape or form.
Skype (Microsoft) is facing fines, criminal and administrative sanctions and
even “a temporary ban on sharing users data with US state agencies”,
according to Softpedia.com, who also said that Luxembourg has vowed to
protect users’ privacy unless state agencies fill in legal requests for a
specific account. Softpedia cites Luxembourg’s data-protection chief, Gerard
Lommel, as having confirmed an investigation is under way.
Skype, founded in 2003, was a success with users who were interested in
privacy because of the encrypted peer-to-peer technology that allowed users
to connect directly over the web rather than through some central server. It
was so trusted that major corporations, banks and other large business
players have employed it as a standard tool for holding video and audio
conferencing with worldwide partners. Meeting where corporations and
companies often discuss sensitive operational proprietary information that
would be of interest to their competitors and of course the US if engaged in
economic manipulation.
Skype cannot be trusted now, no matter how many times Microsoft says it is
committed to protecting users’ privacy and the real losers of the free
service are now the users.
Personally it is a real shame because I used to use Skype to talk to all
sorts of people and it is a wonderful tool. I even use it to stay in touch
with one of my best friends in the UK. We suspected all along that all of
our communications were being monitored but thanks to Edward Snowden, we now
know this to be true. We now begin every conversation with “Hello NSA
analyst”, and are sympathetic that some poor guy has to listen to our
conversations and can not join in even though we invite them to speak up.
Even NSA analysts should have a voice.
Last Update: 11/19/2023 20:00 -0000
Please help keep us going and make a donation Thanks to all supporters! PayPal, Сбербанк Sberbank Visa 4276 3800 4476 1661 Copyright JAR2 2003-2103 All Rights Reserved Publishing Banned Truth Since June 06, 2003
|